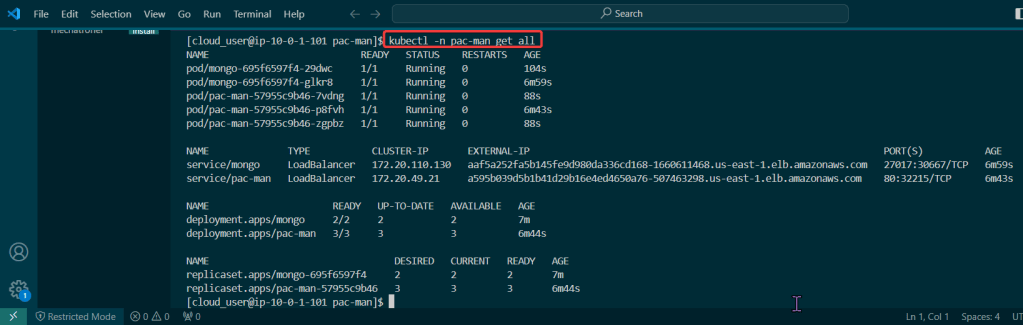
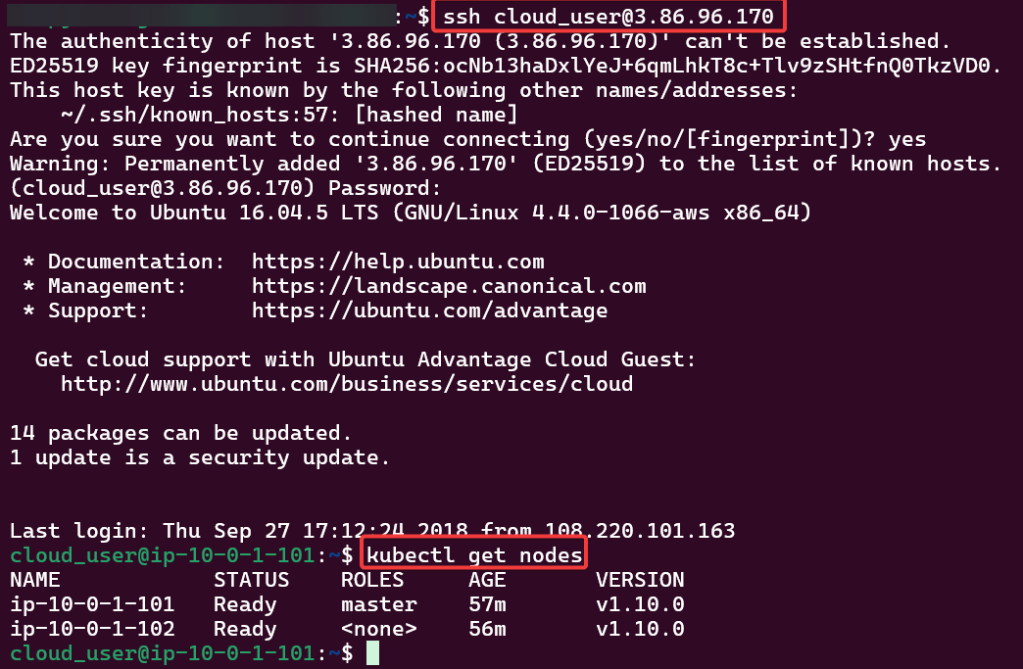
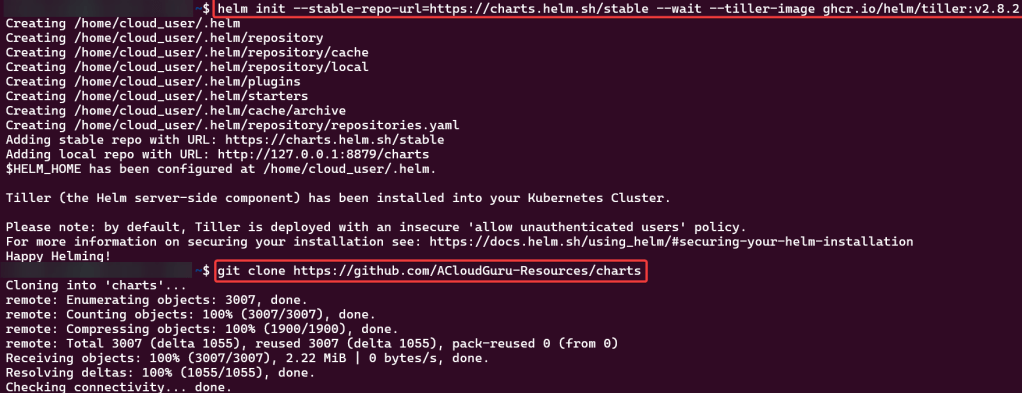
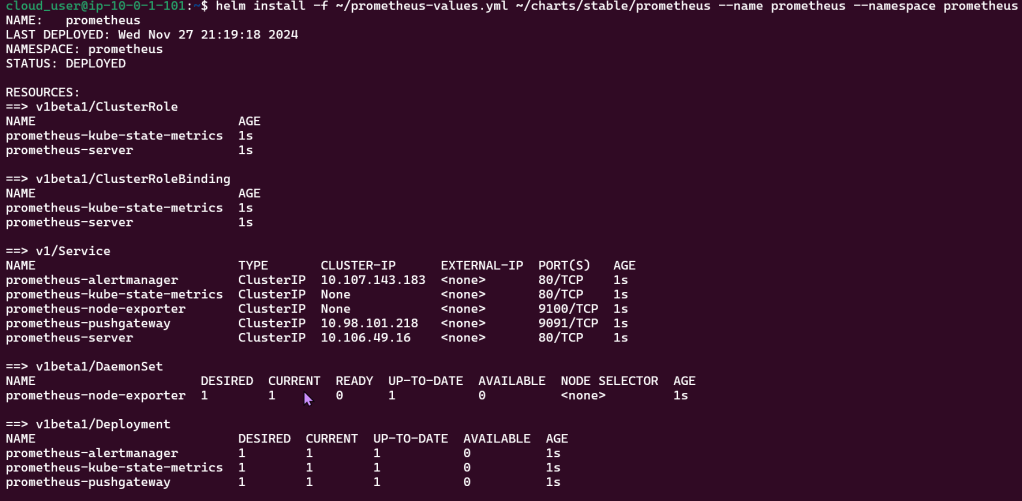
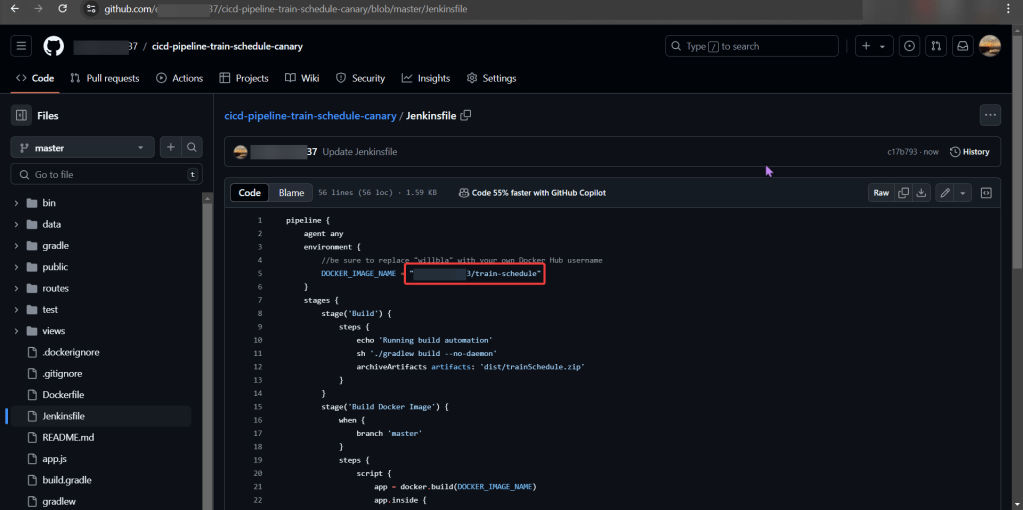
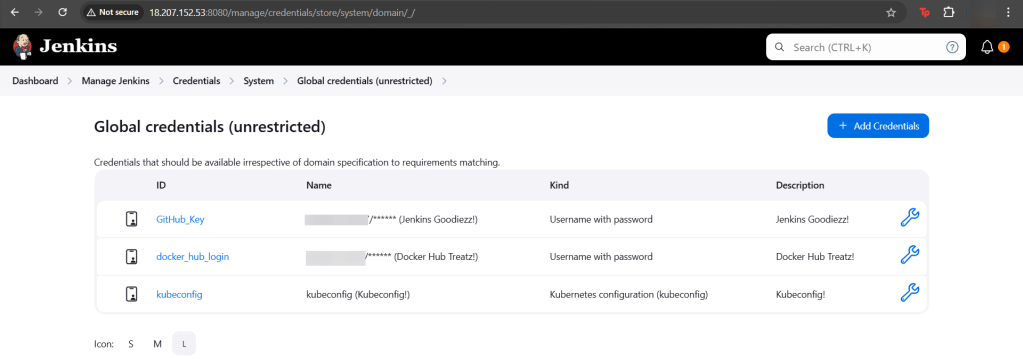
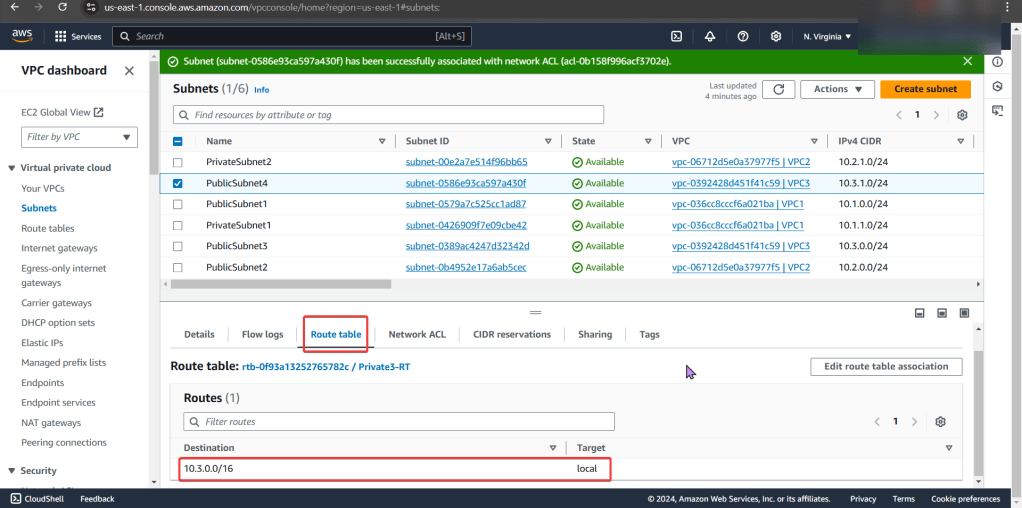
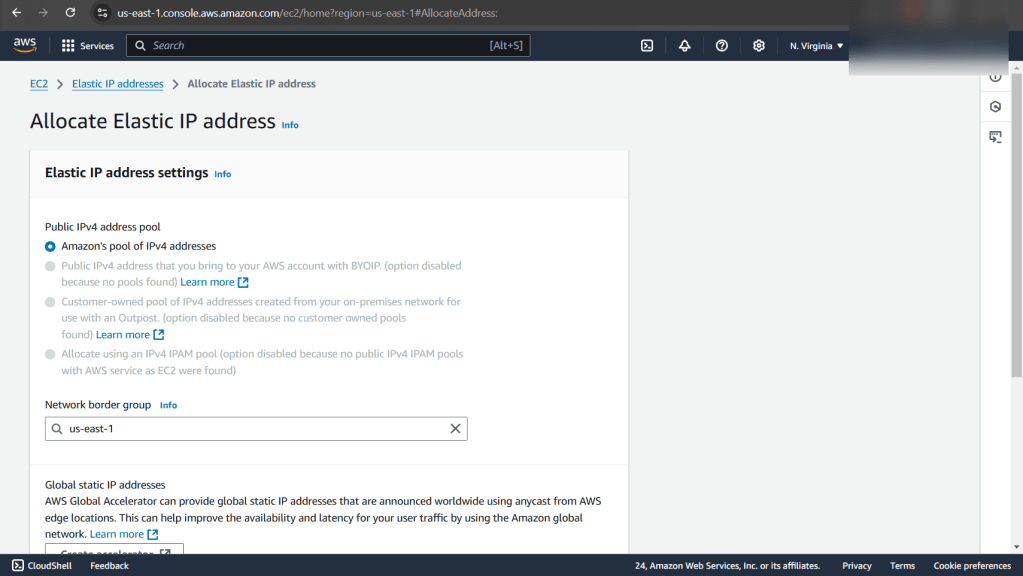
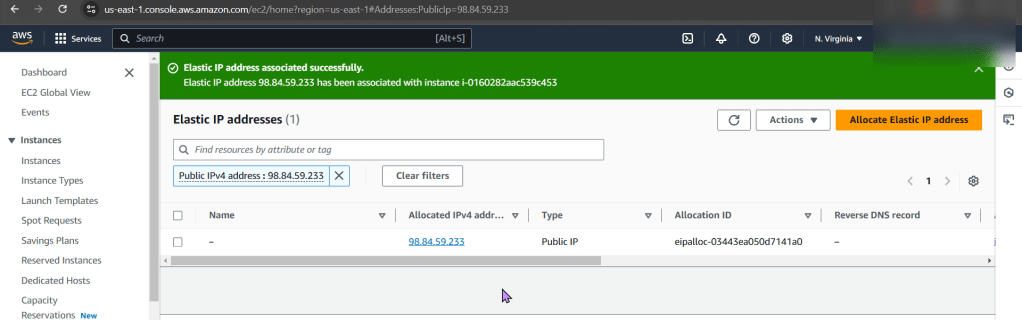
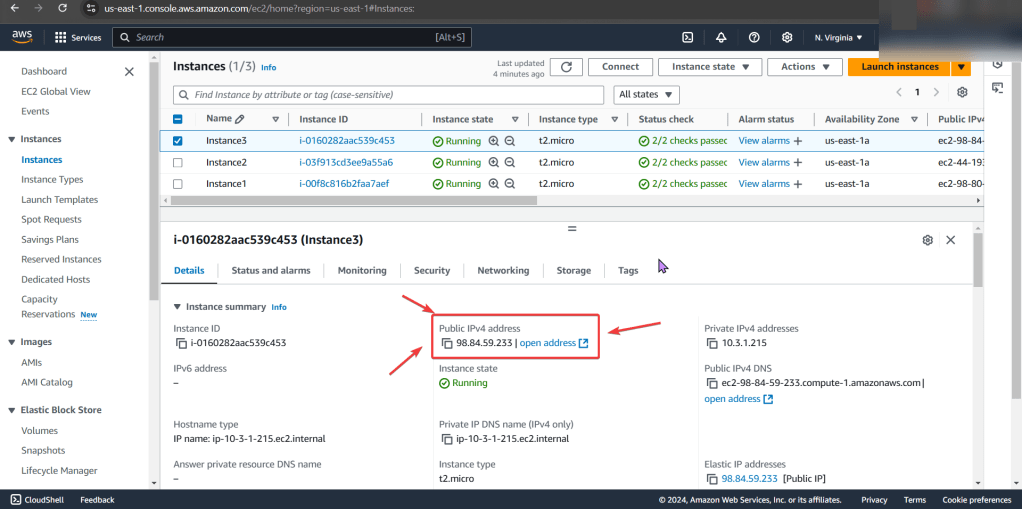
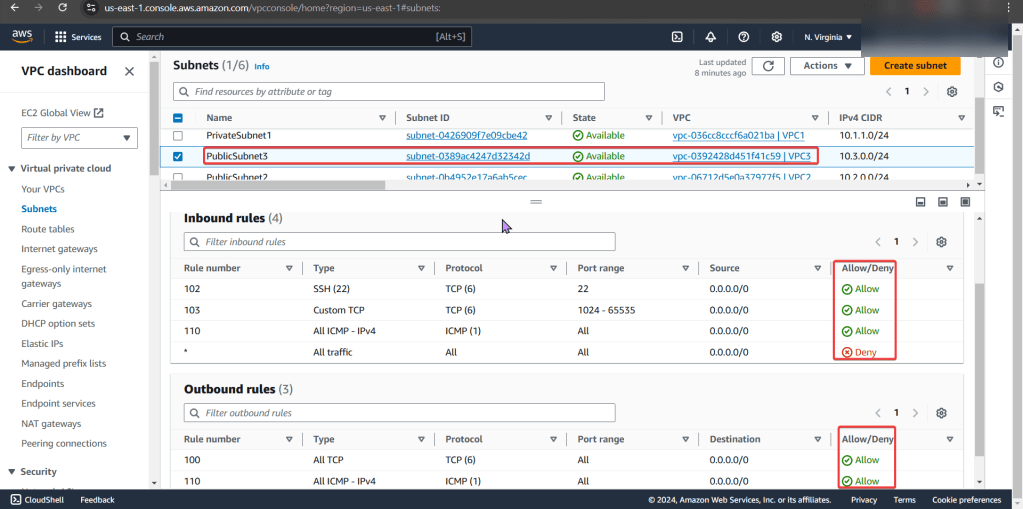
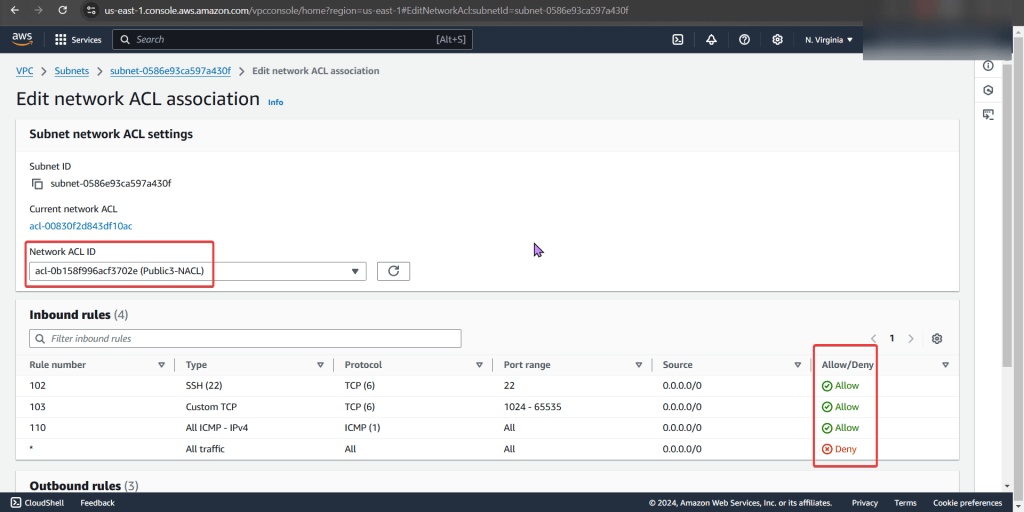
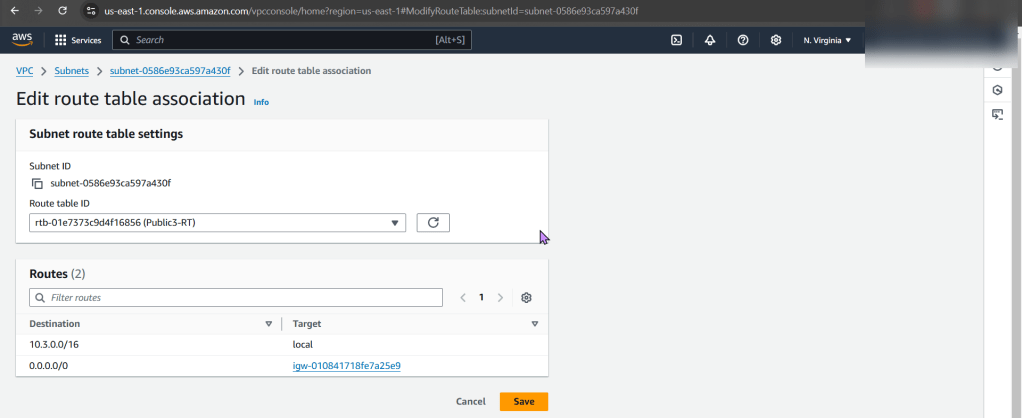
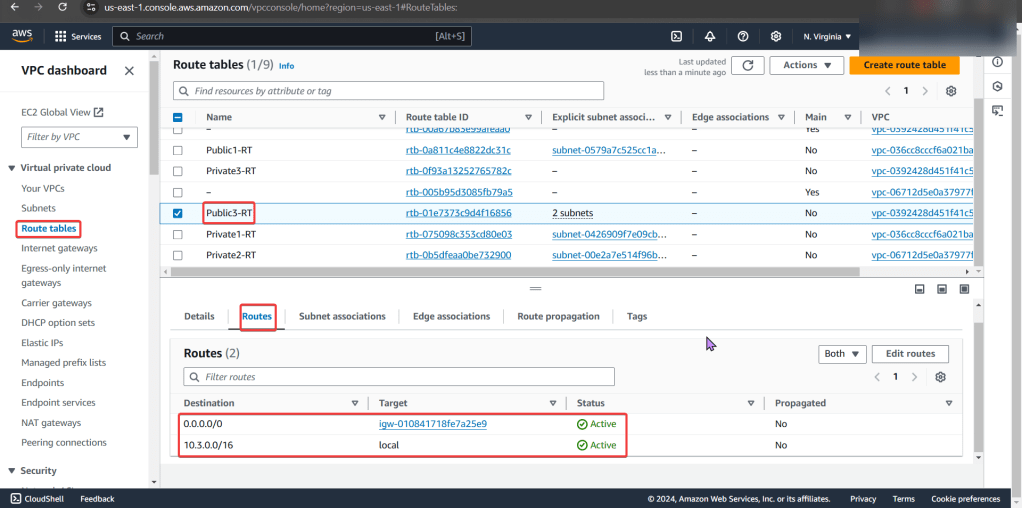
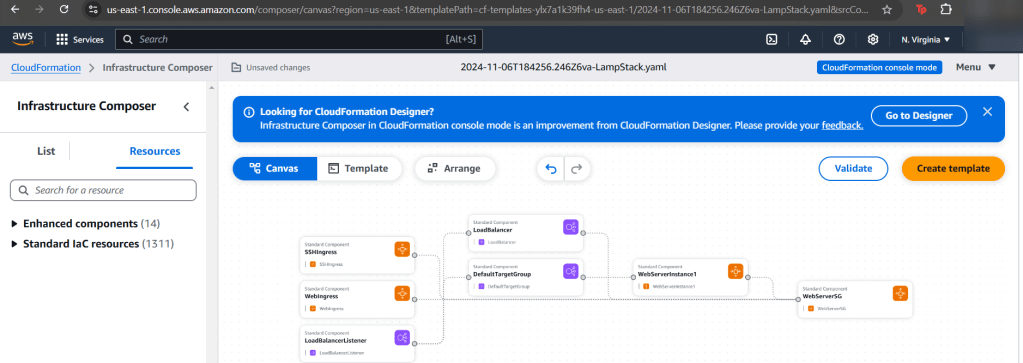
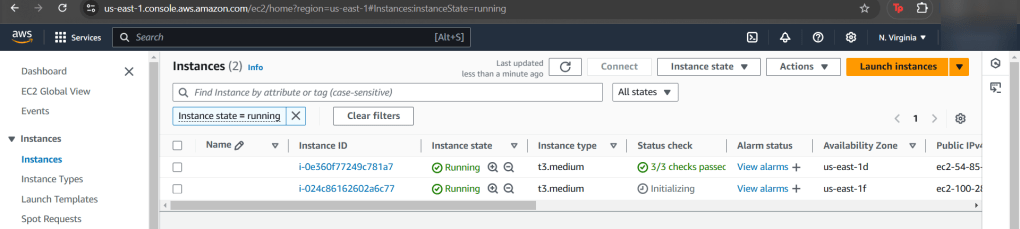
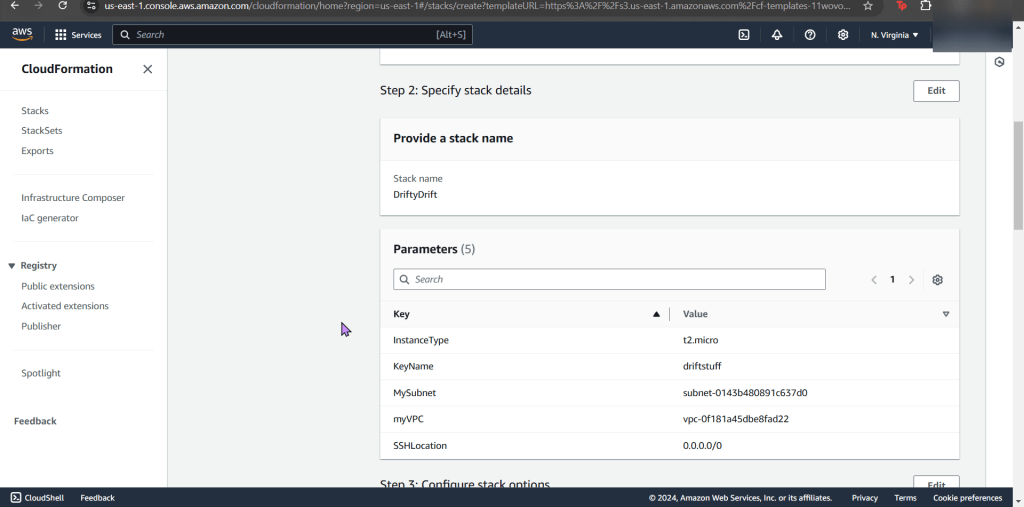
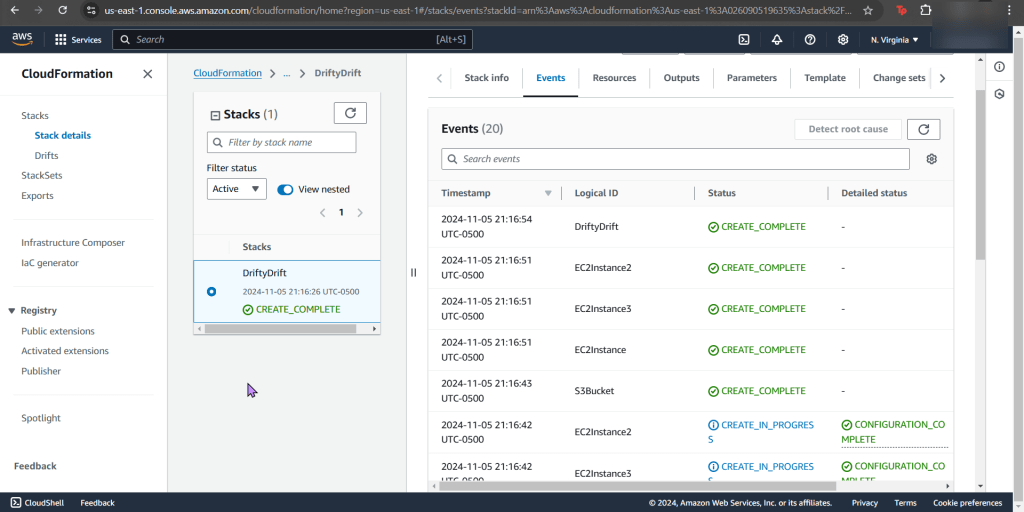
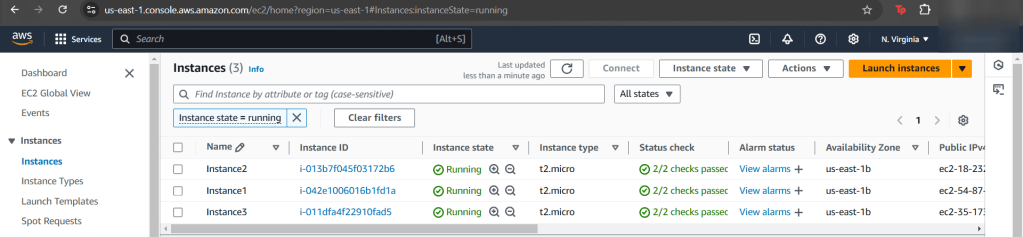
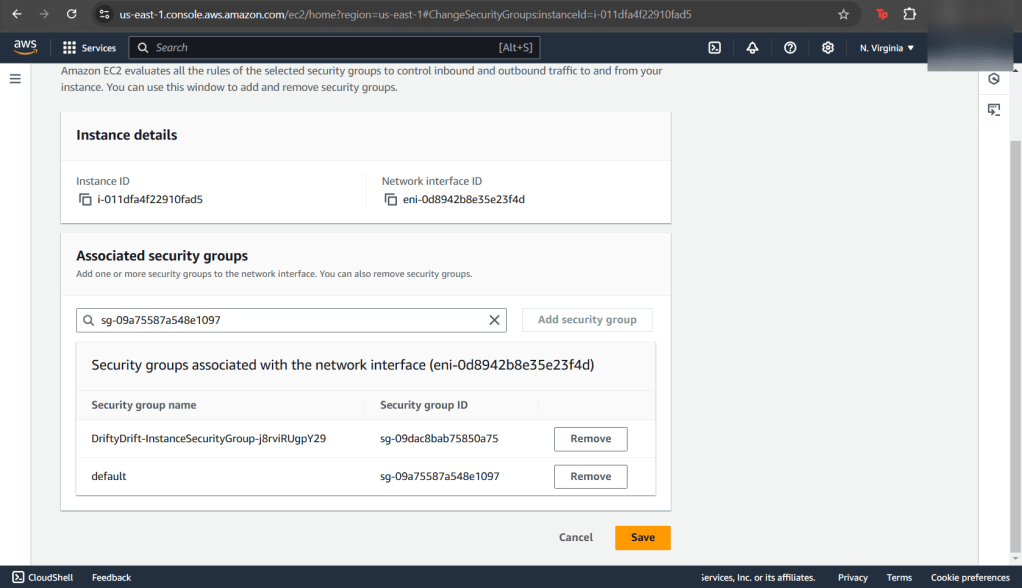
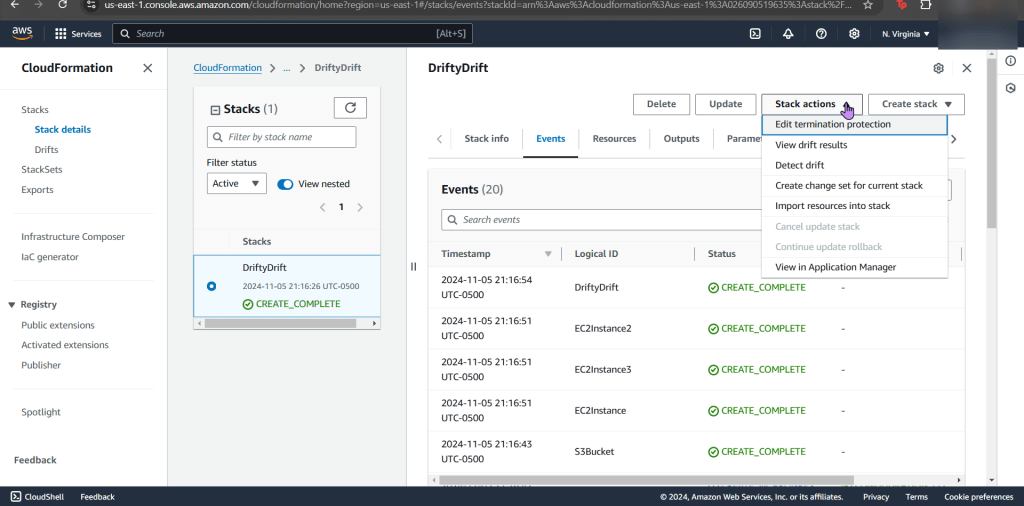
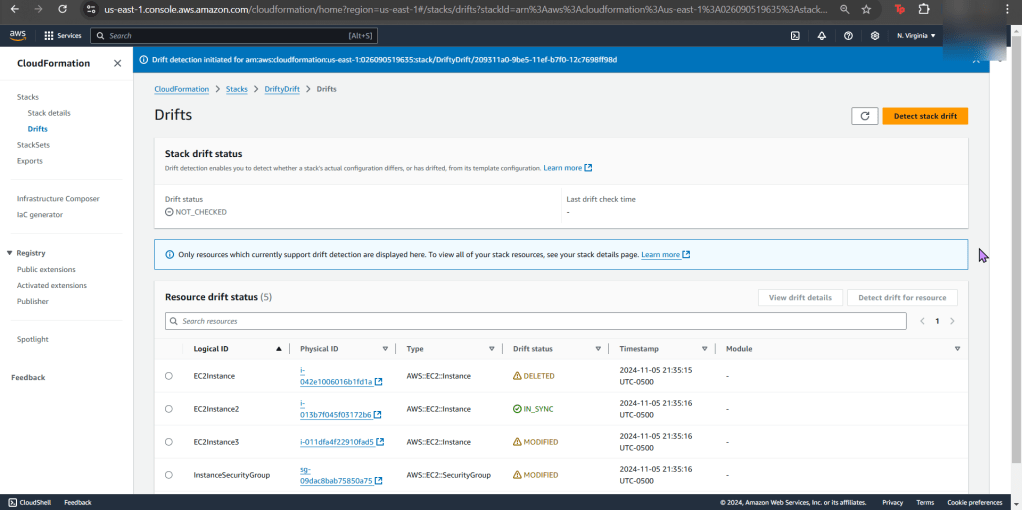
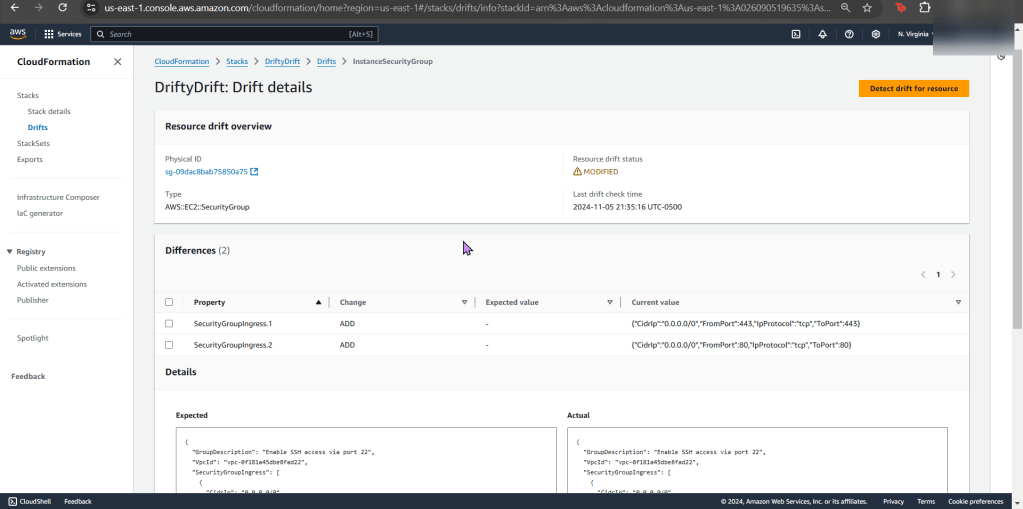
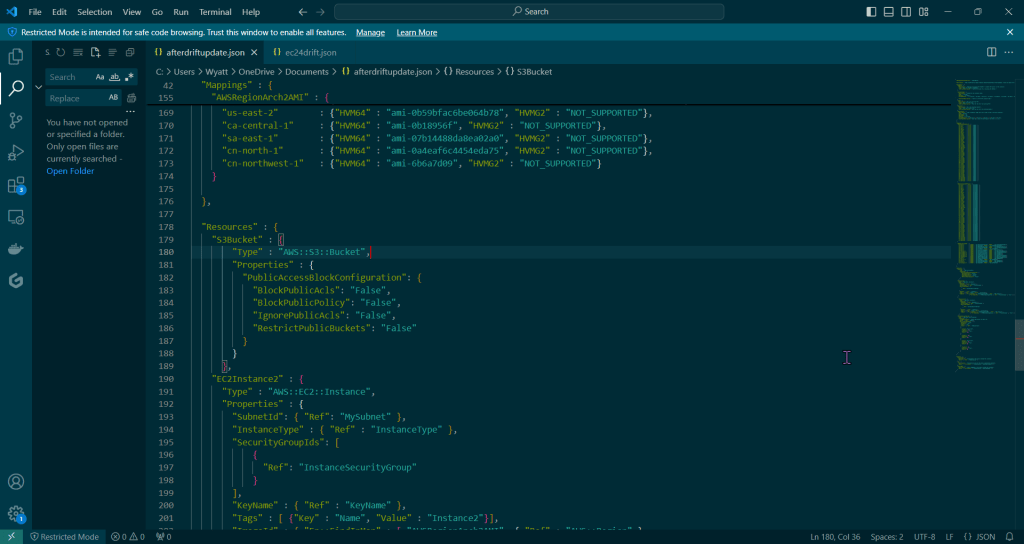
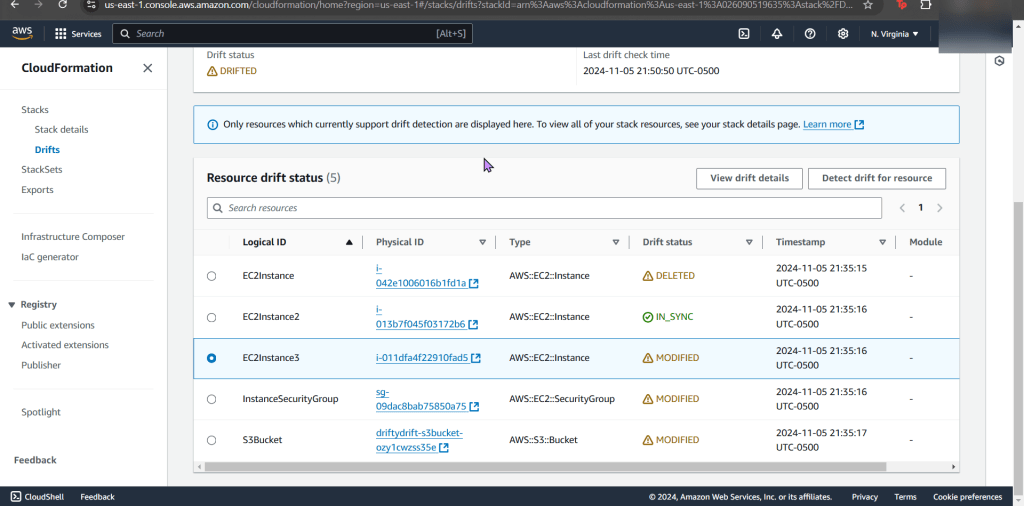
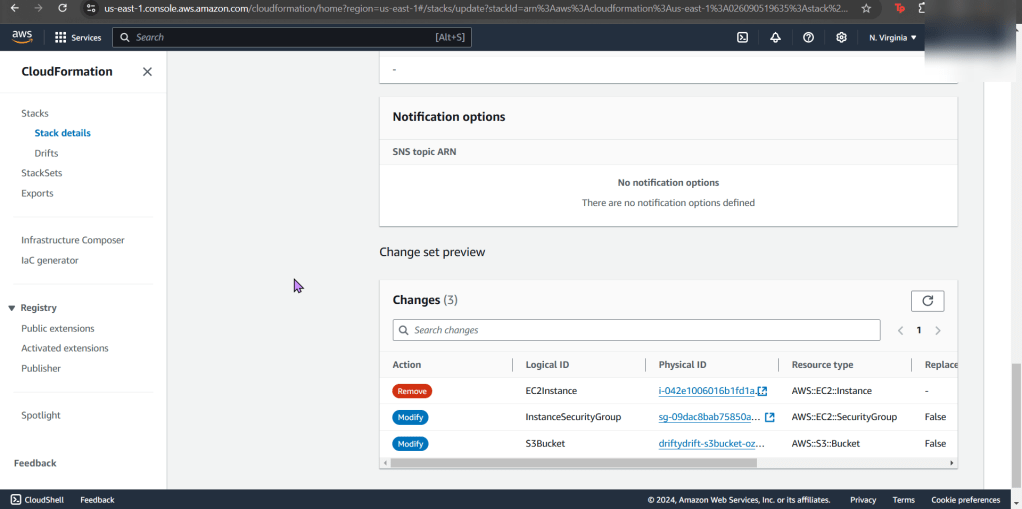
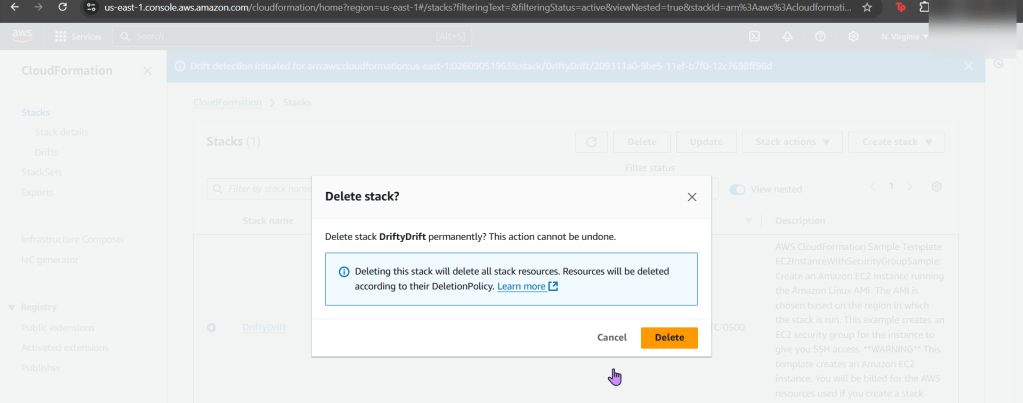
Goal:
Falco Lombardi is… ahem.. Falco is able to detect any shady stuff going on in your Kubernetes environment in no time.

Lessons Learned:
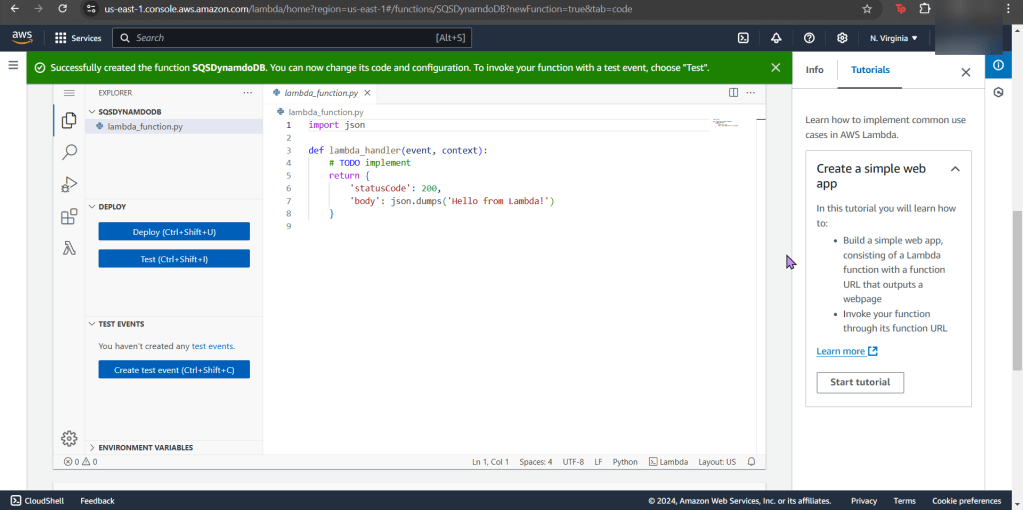
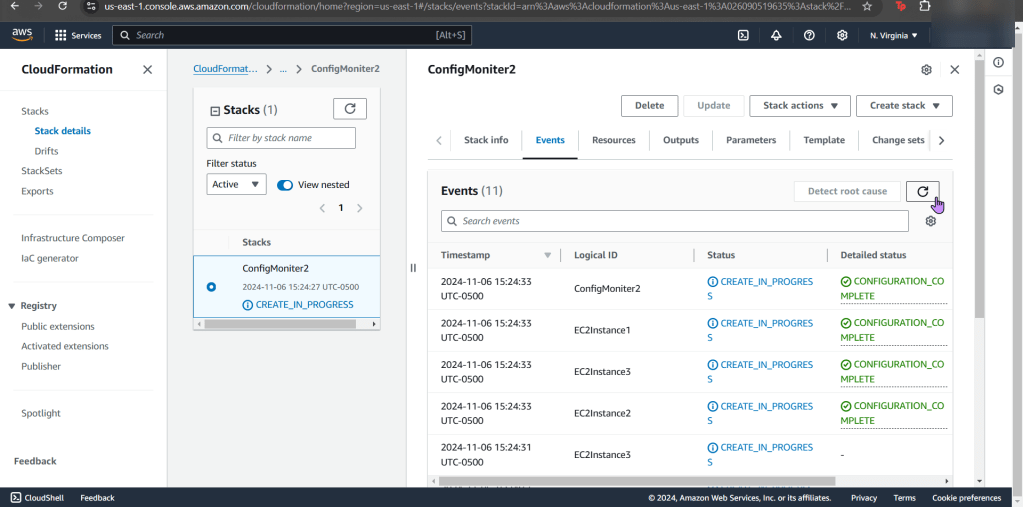
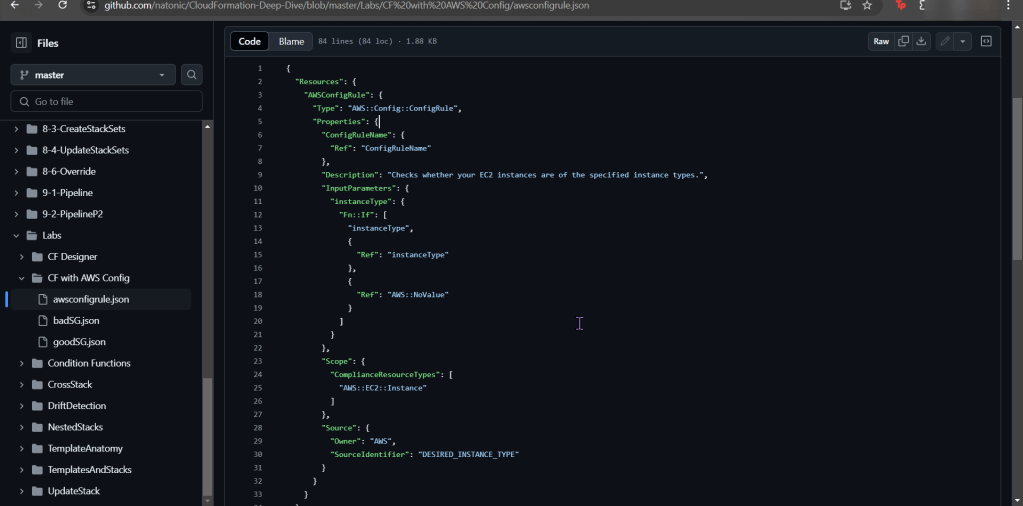
- Create a Falco Rules File to Scan the Container
- Run Falco to Obtain a Report of ALL the Activity
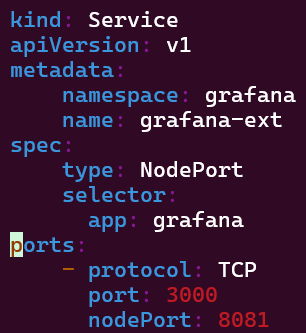
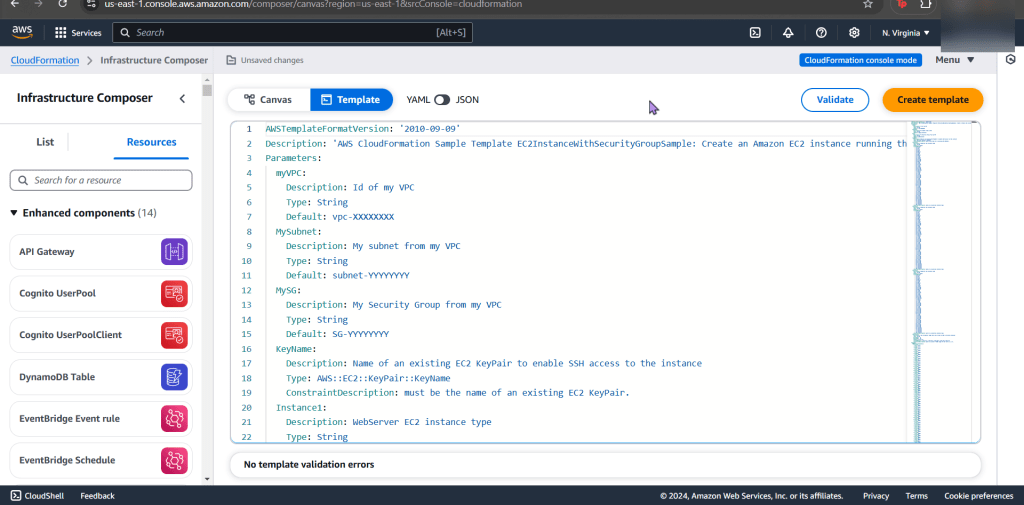
Create a Falco Rules File to Scan the Container
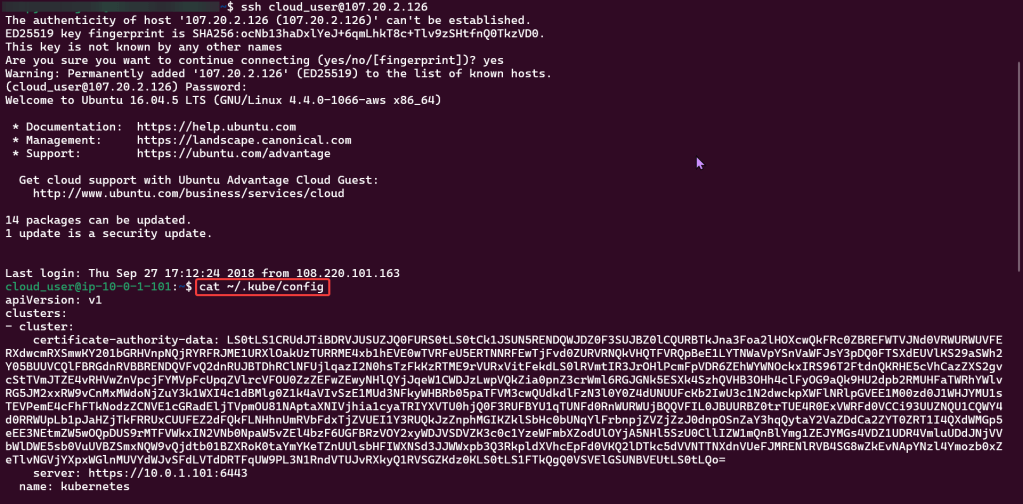
SSH:
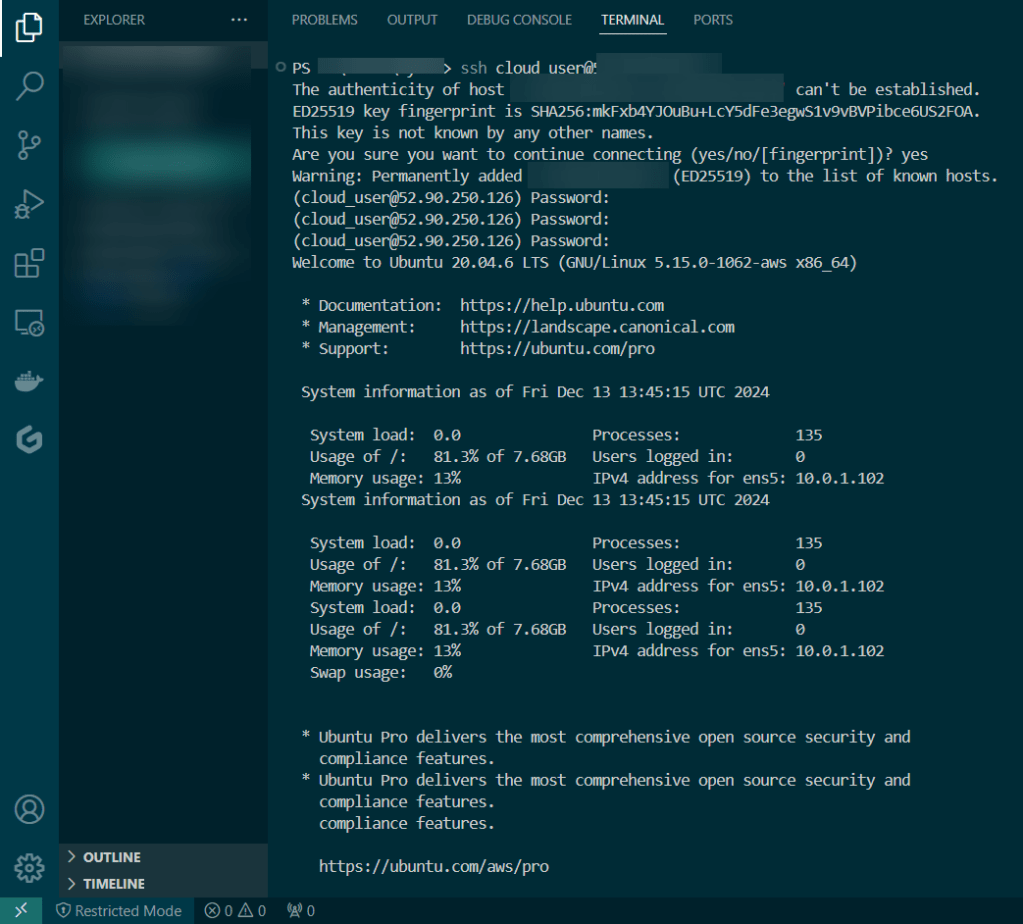
Vi nginx-rules.yml:
- Create rule to scan container, basically this scripts rule will:
- Rule:
- Detects if a new container is created
- Desc:
- Says just that…
- Condition:
- Looking for new process w/an event type to detect if changes occur w/in the container nginx
- Output:
- How the event is posted once complete
- Rule:

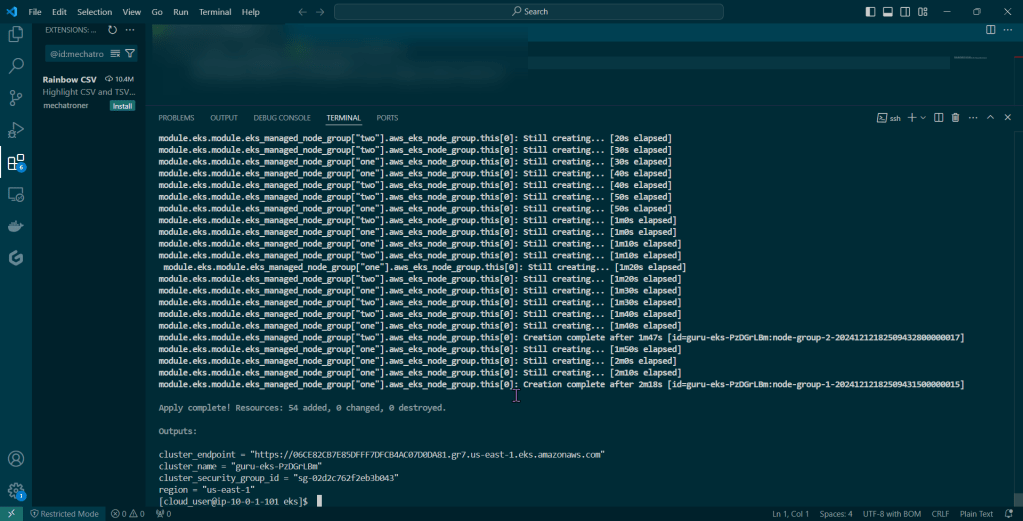
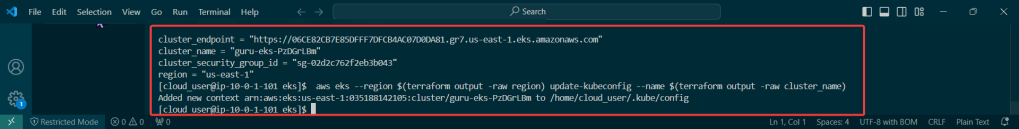
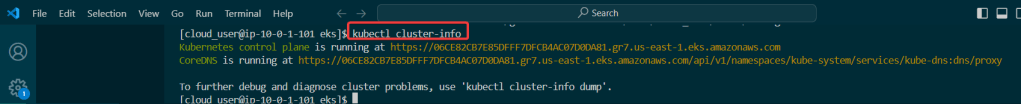
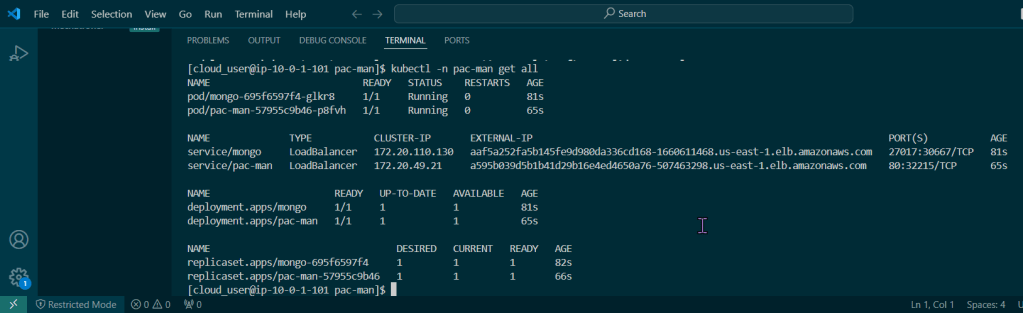
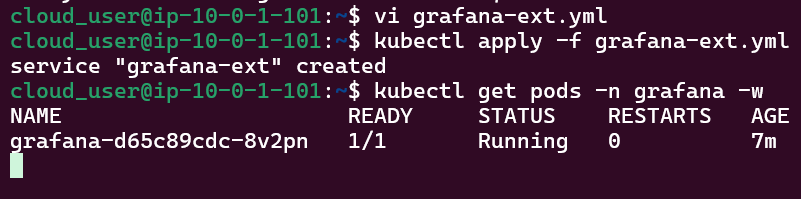
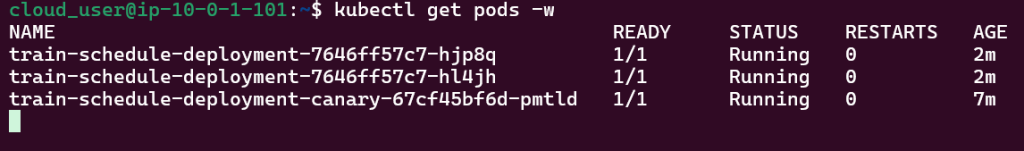
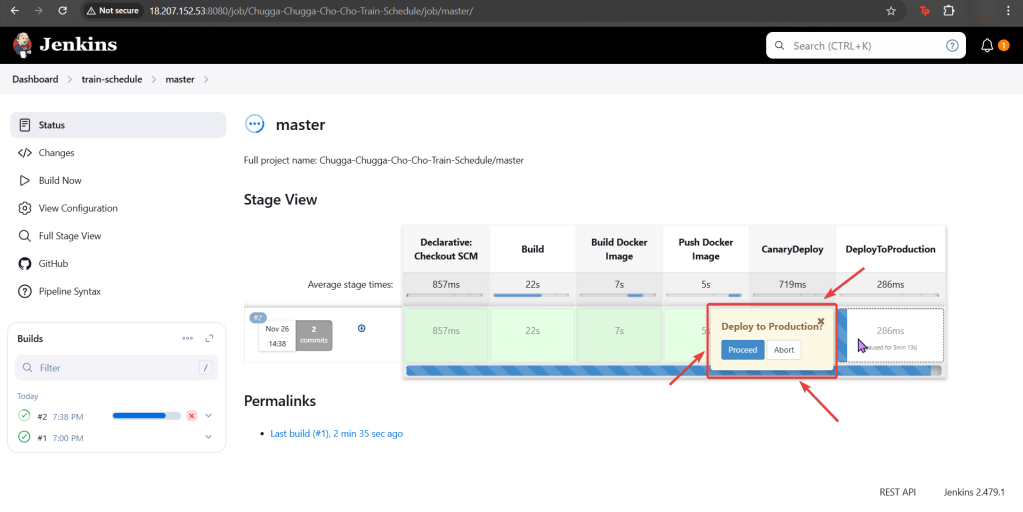
Run Falco to Obtain a Report of ALL the Activity:
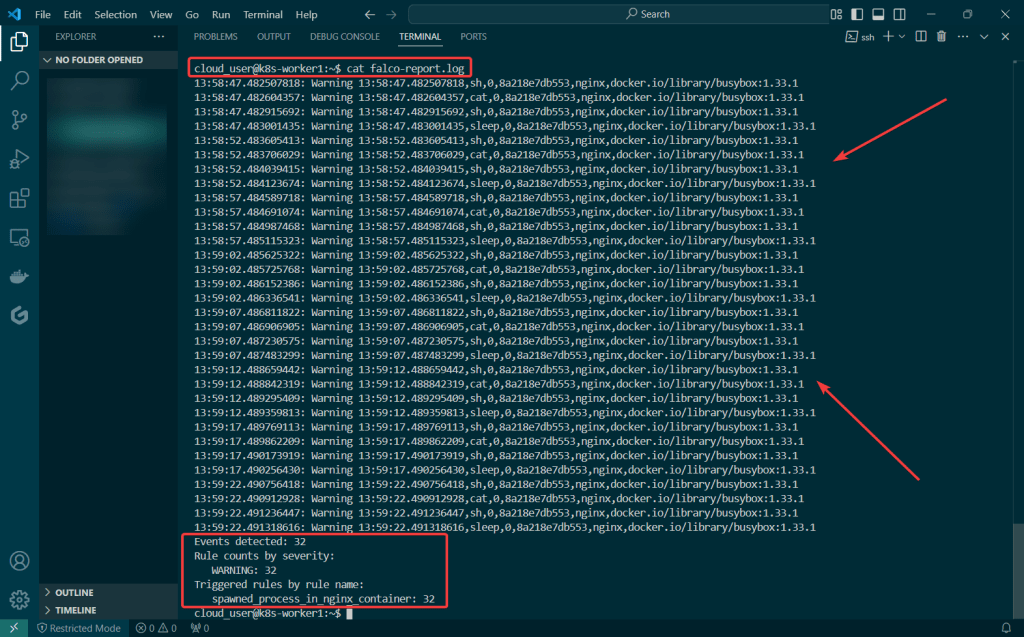
Sudo falco -r nginx-rules.yml -M – 45
- Run Falco for up to a minute & see if anything is detected
- -r = rule
- -M = time
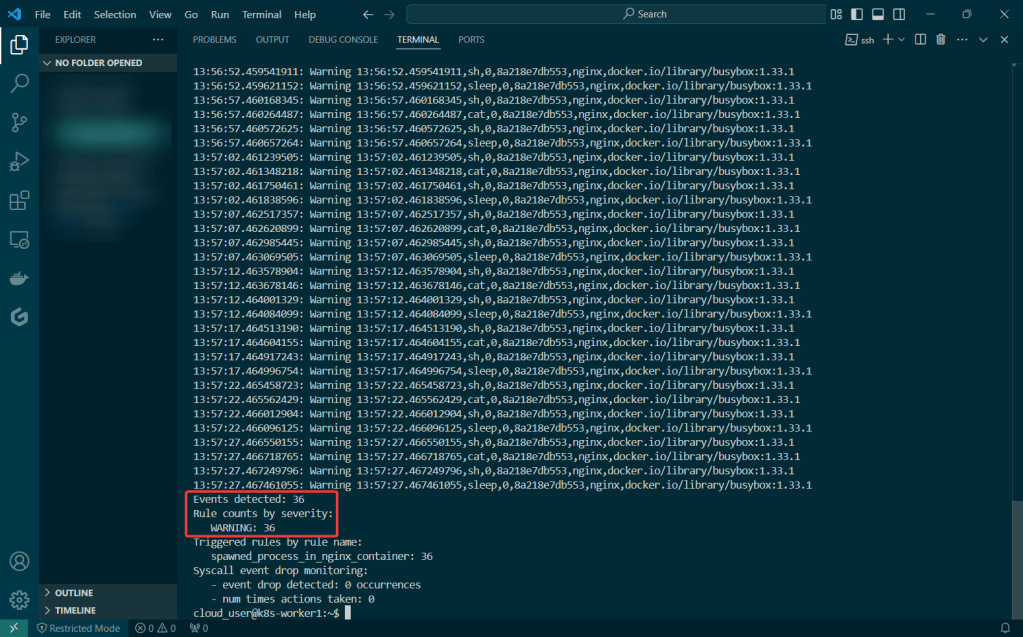
Sudo falco -r nginx-rules.yml -M – 45 > falco-report.log: