Goal:
DO YOU HAVE A KUBERNETES CLUSTER! IS IT INSECURE!? …. I’m out of breath & getting dizzy, Idk how those commercials bring that outside voice & energy – – its exhausting!
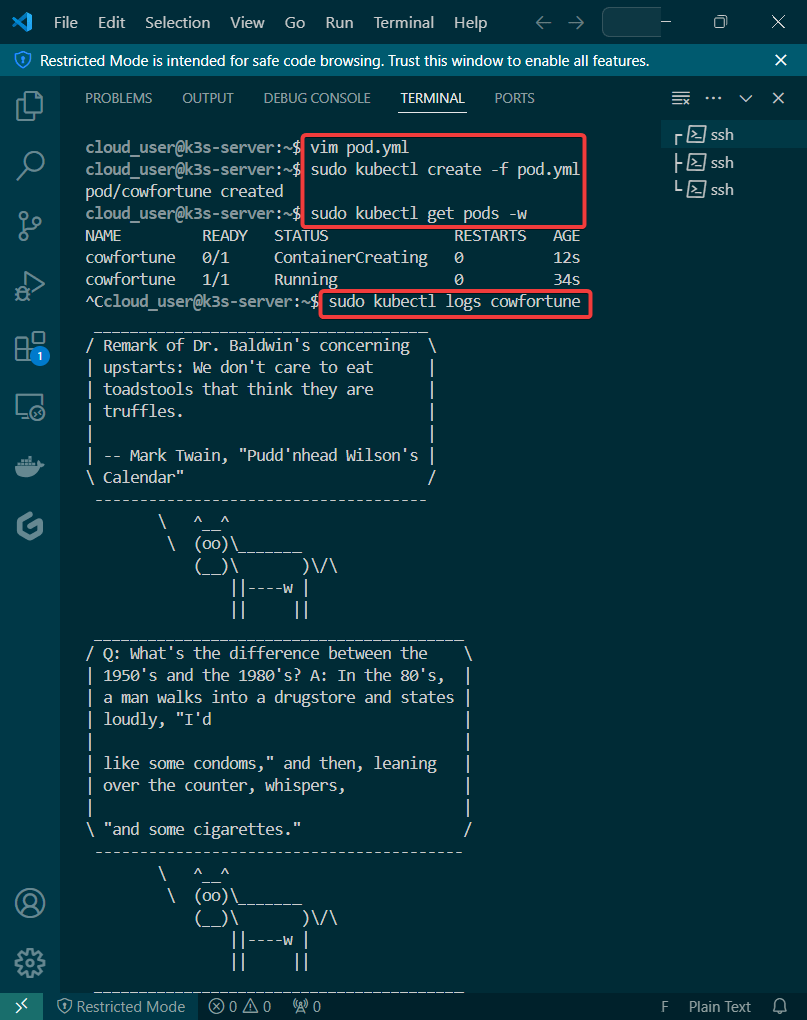
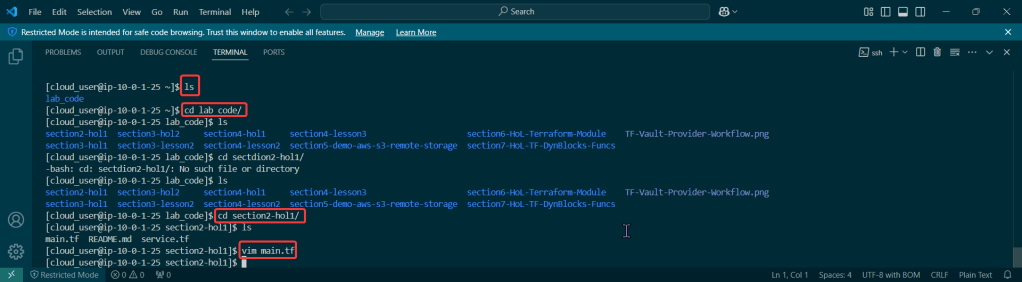
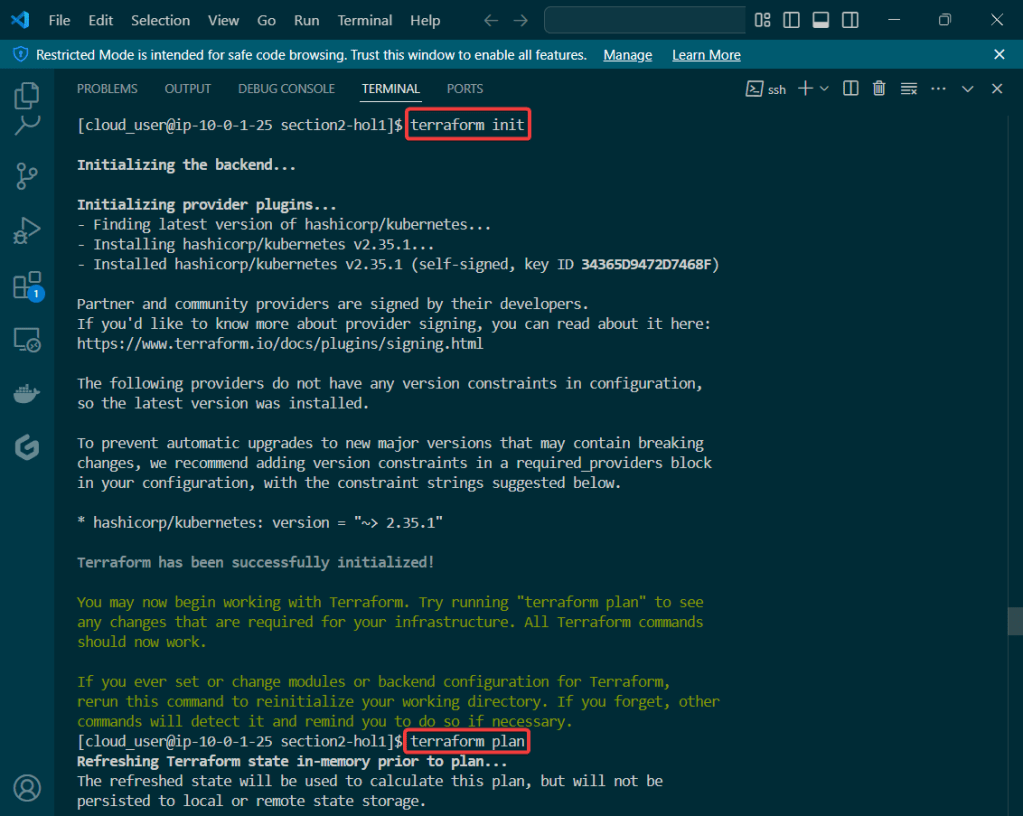
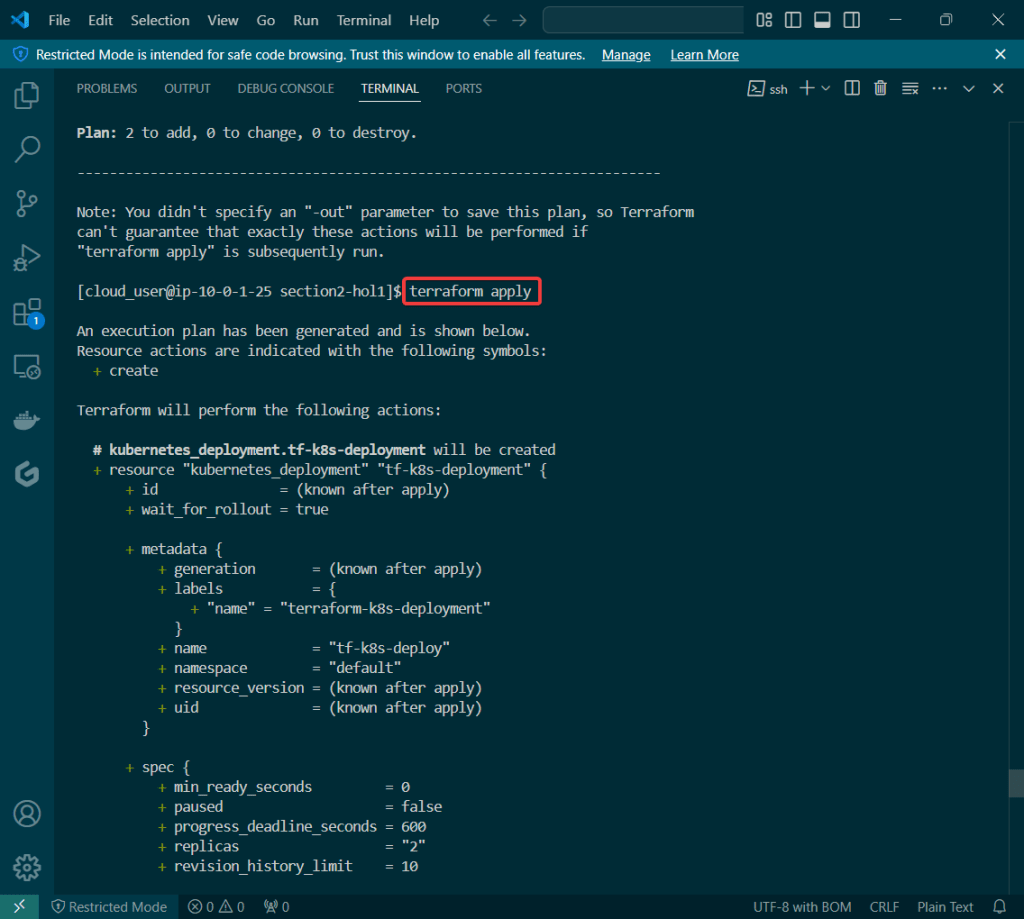
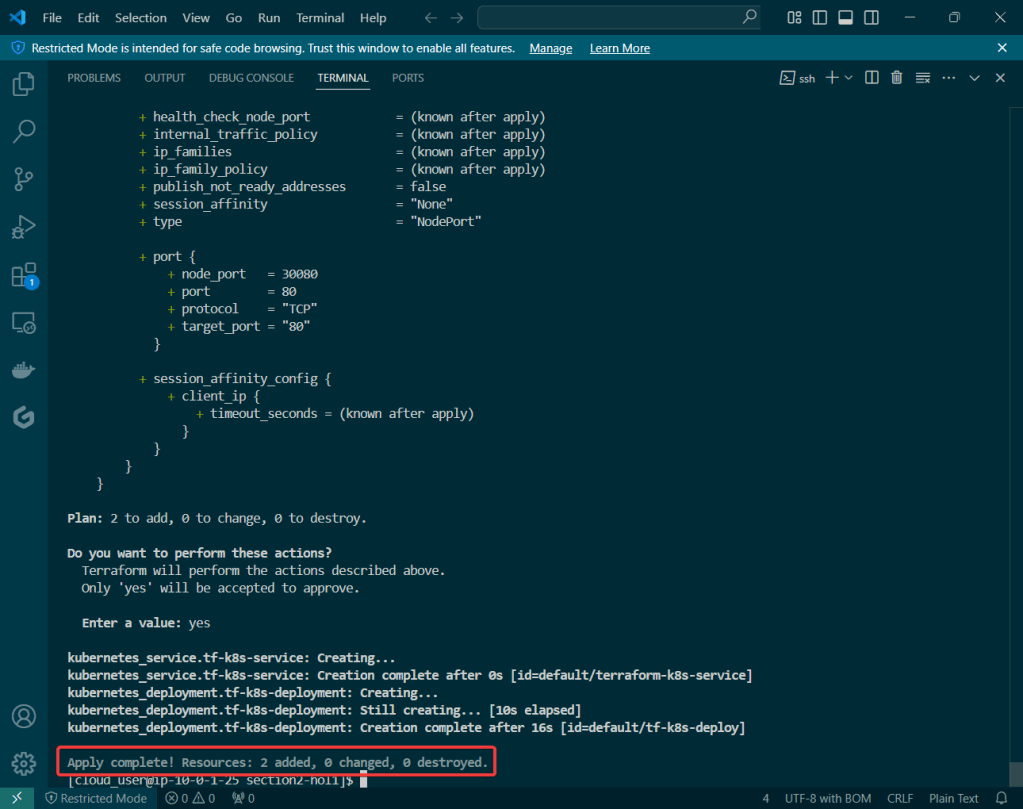
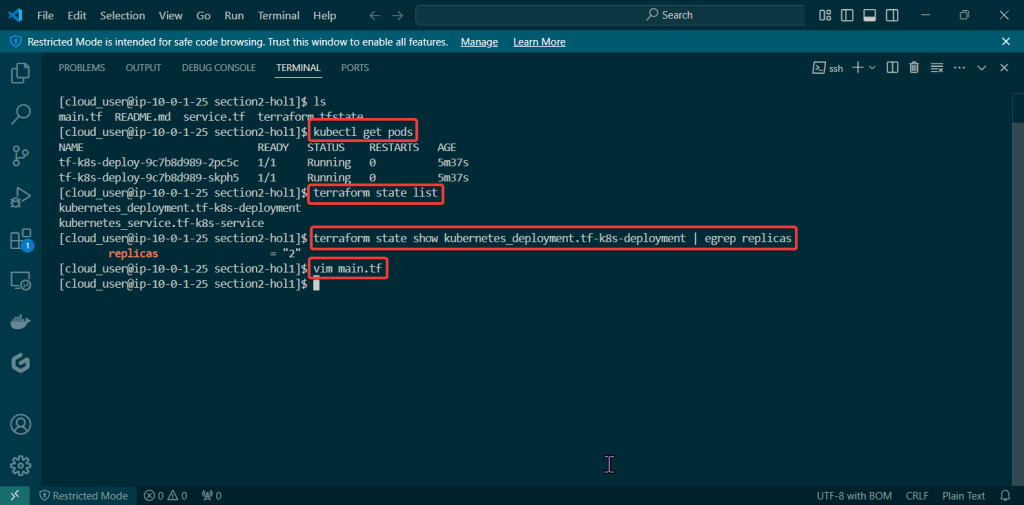
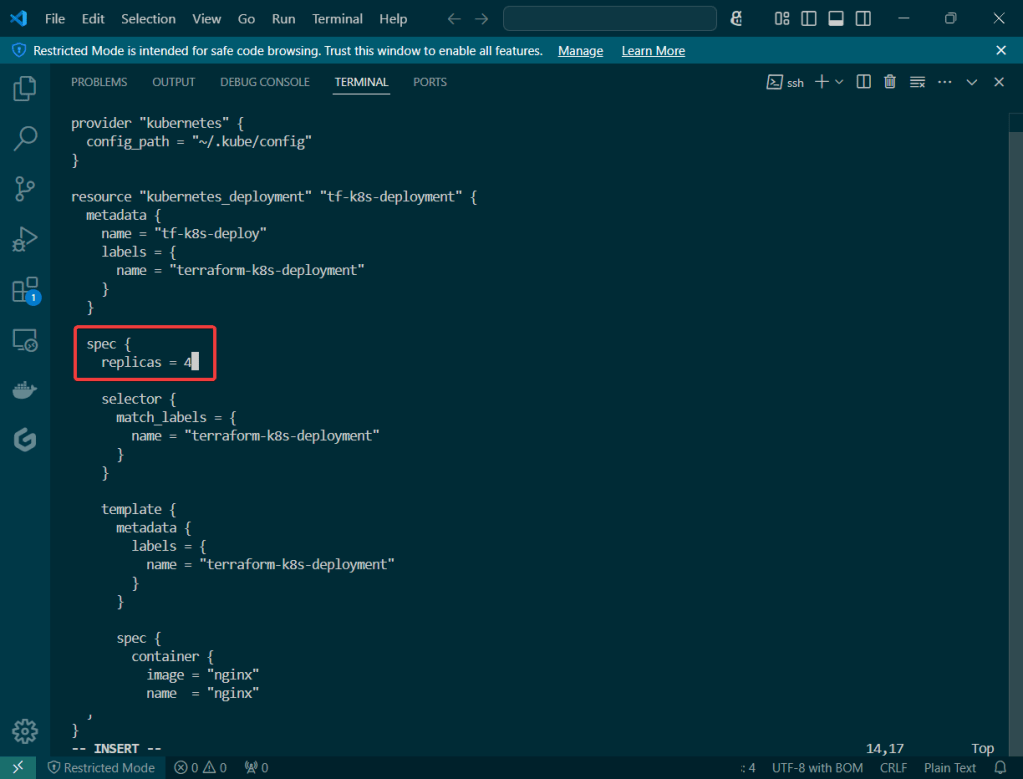
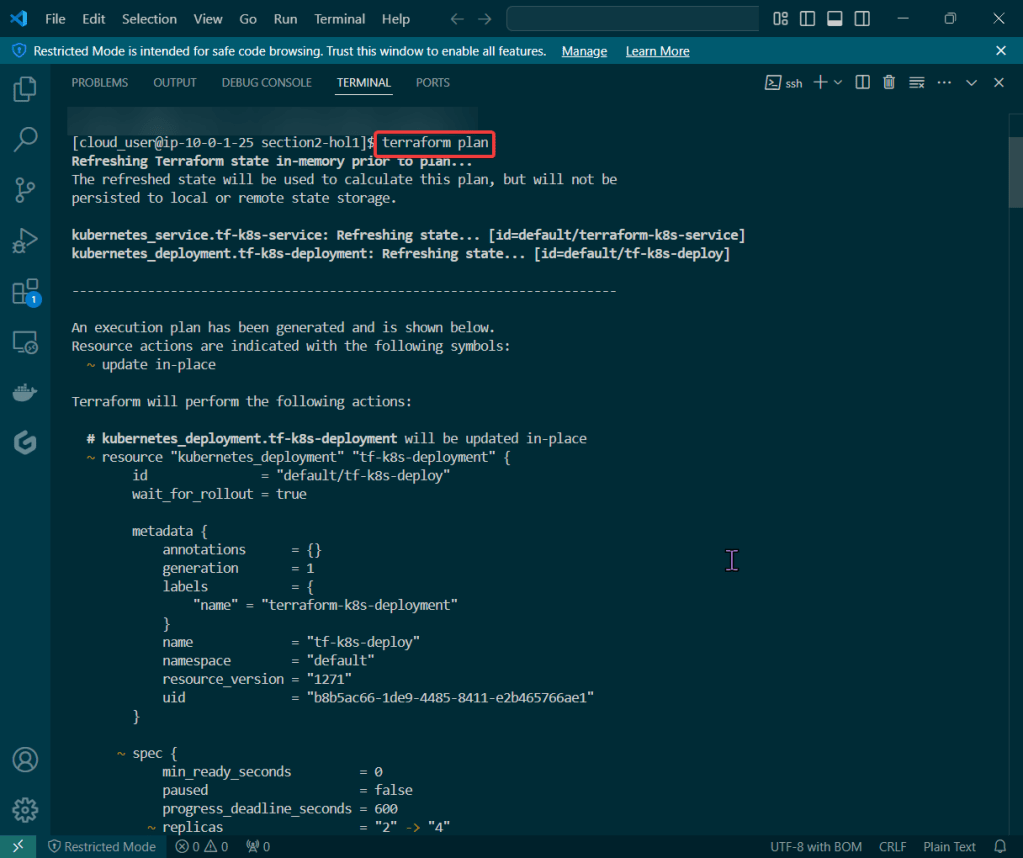
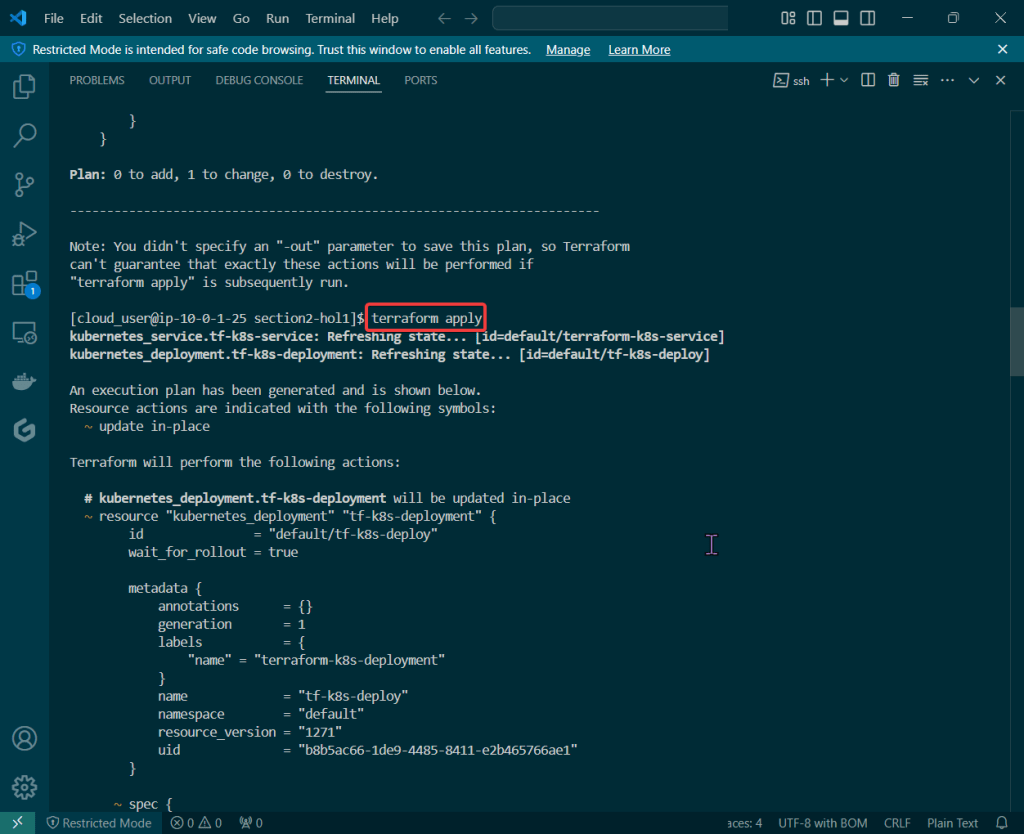
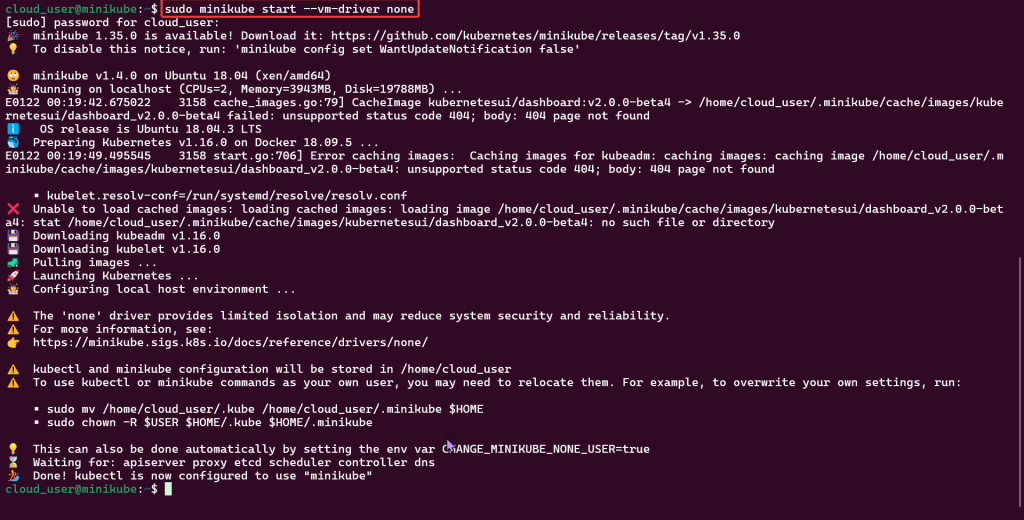
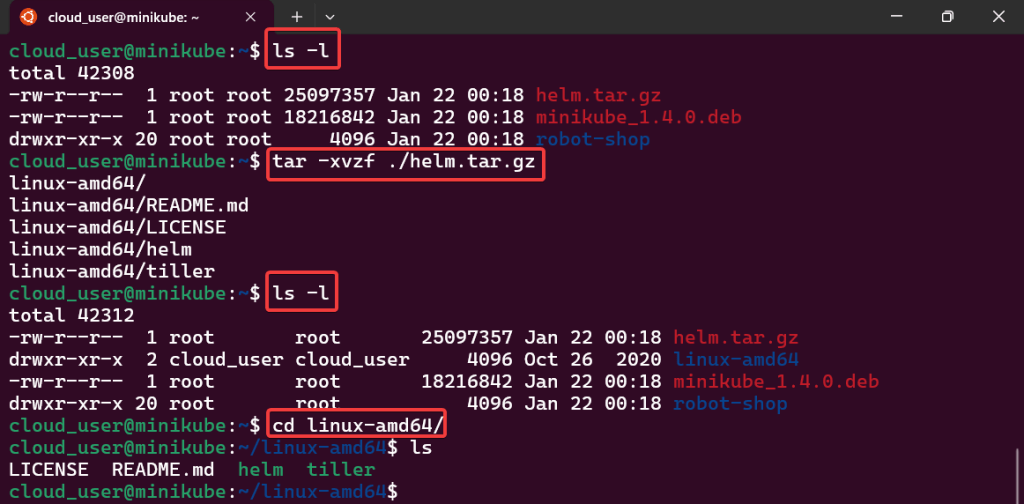
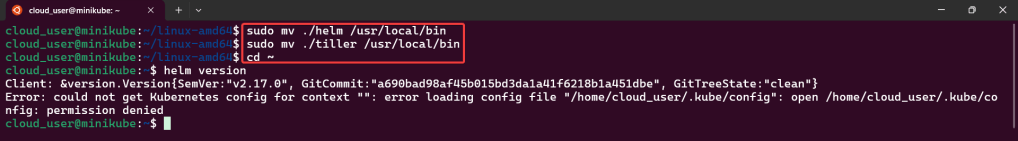
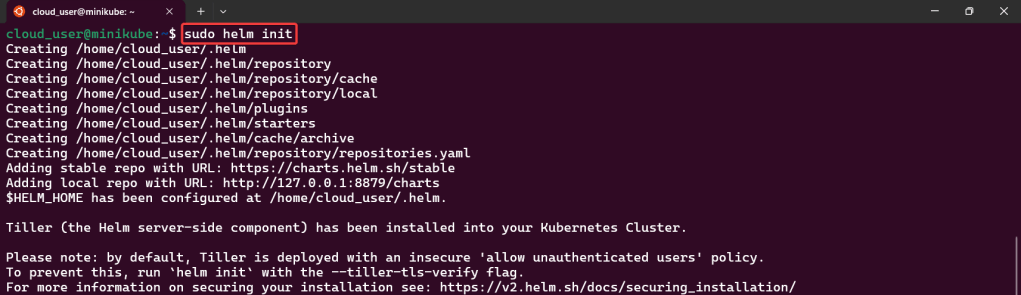
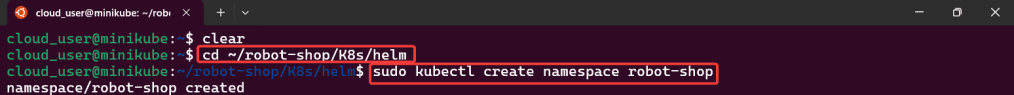
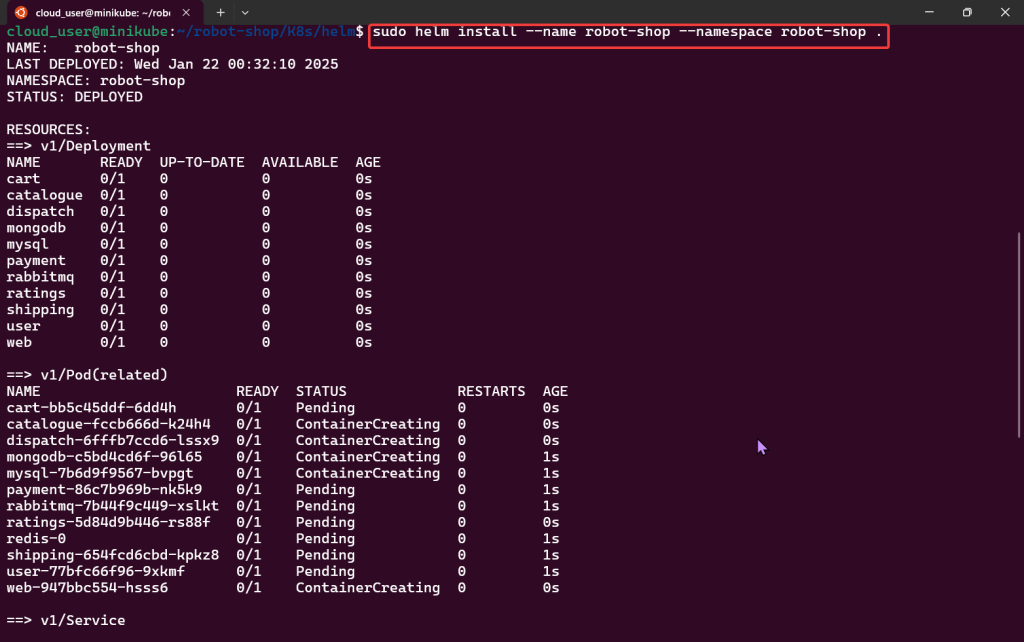
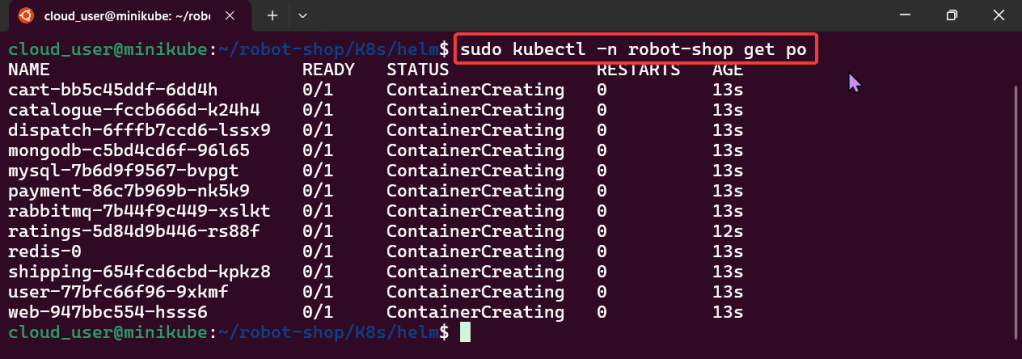
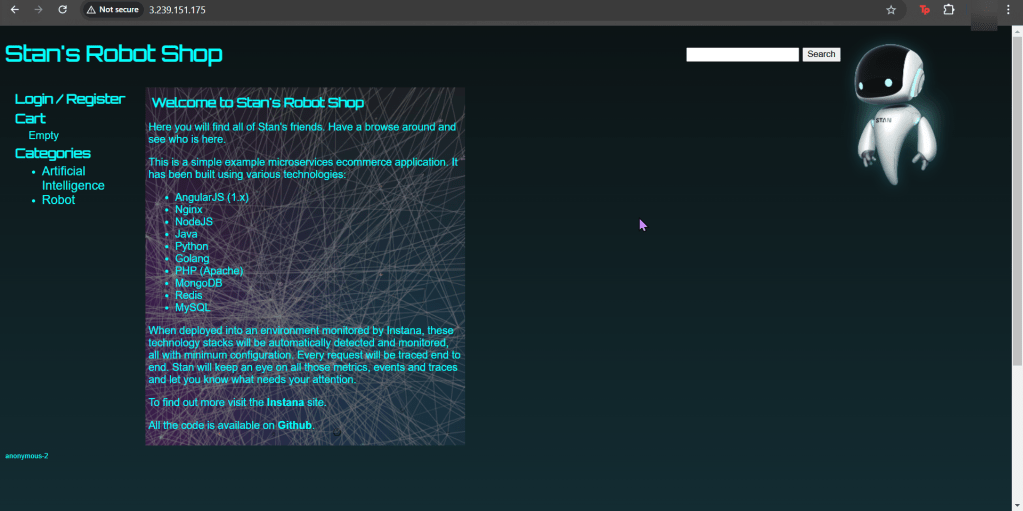
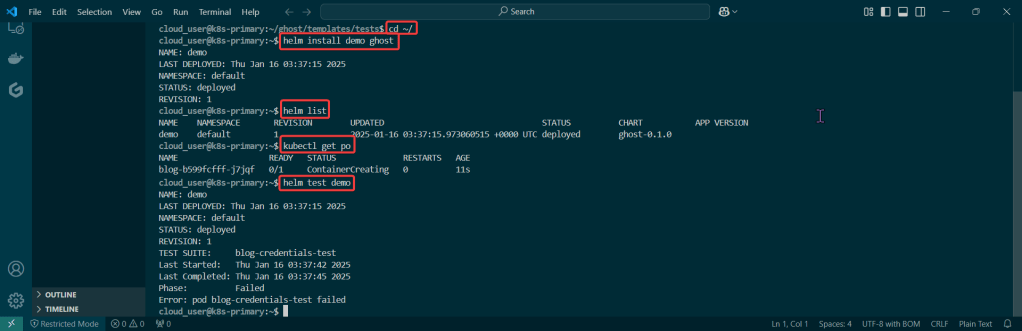
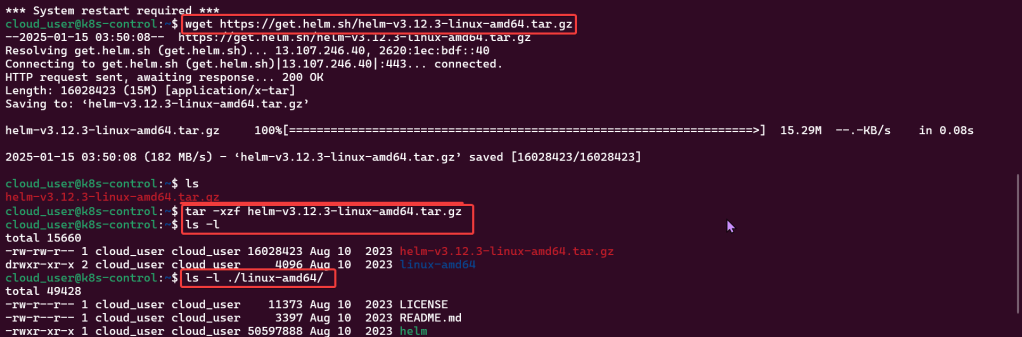
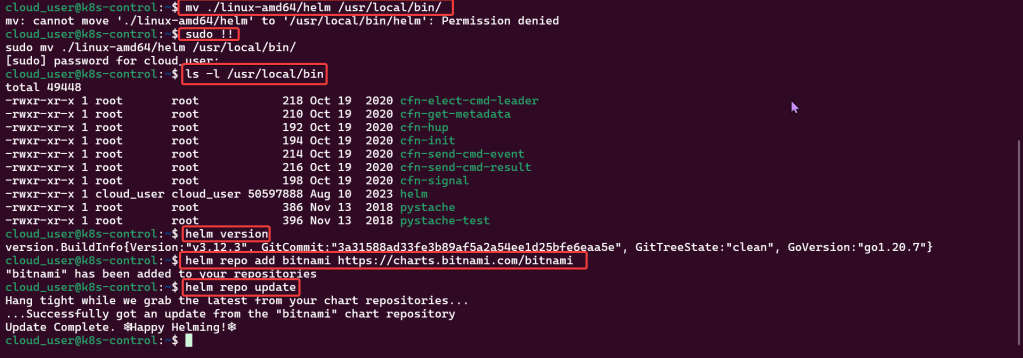
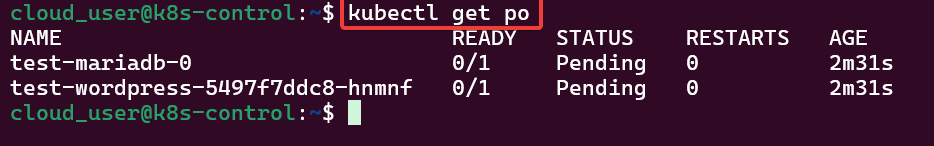
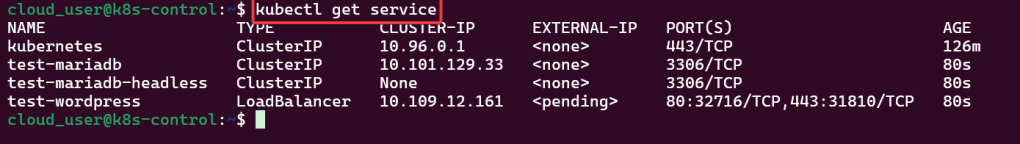
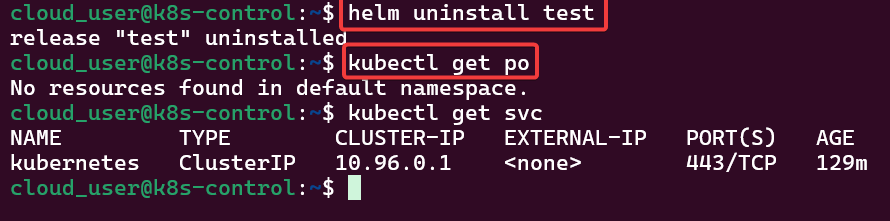
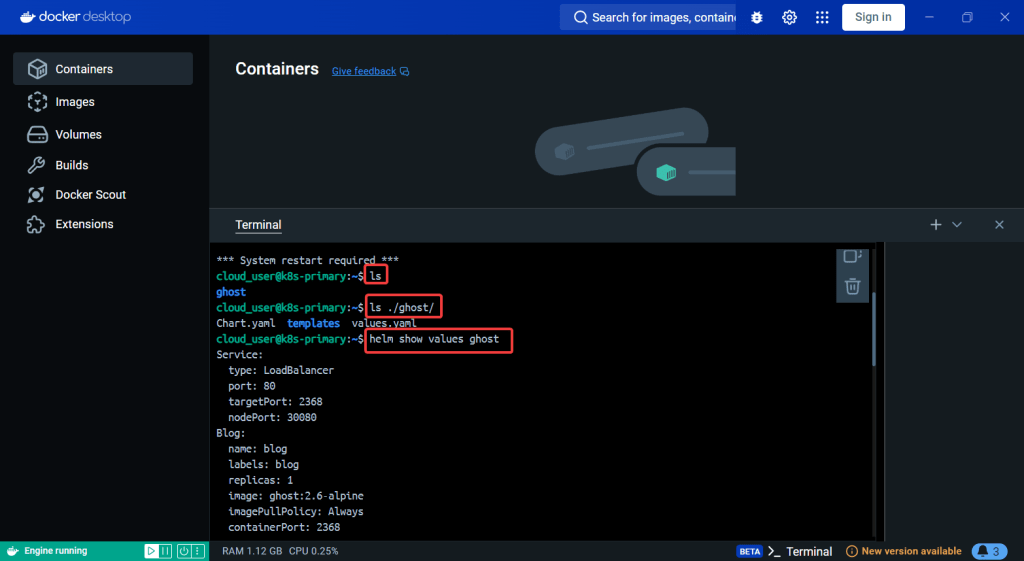
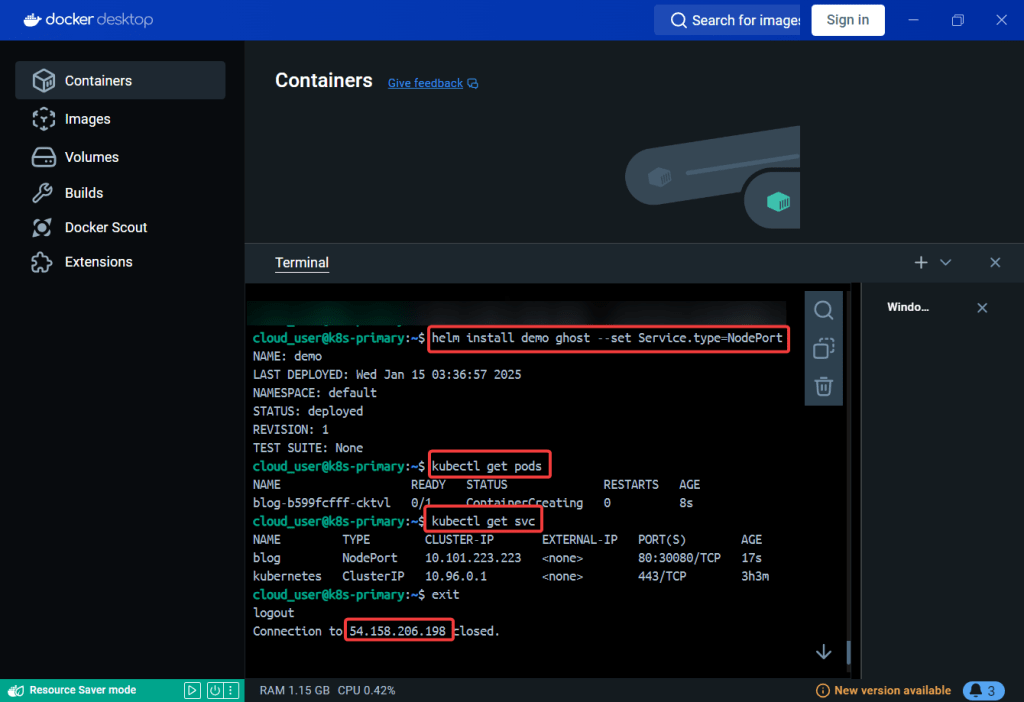
Alright, I’m back – all this will show you is how to secure your cluster. Below you can see how one can authenticate w/one another’s Kubernetes after you have a certificate & attach a certificate authority (CA) by creating certificate’s to bootstrap your Kubernetes cluster.
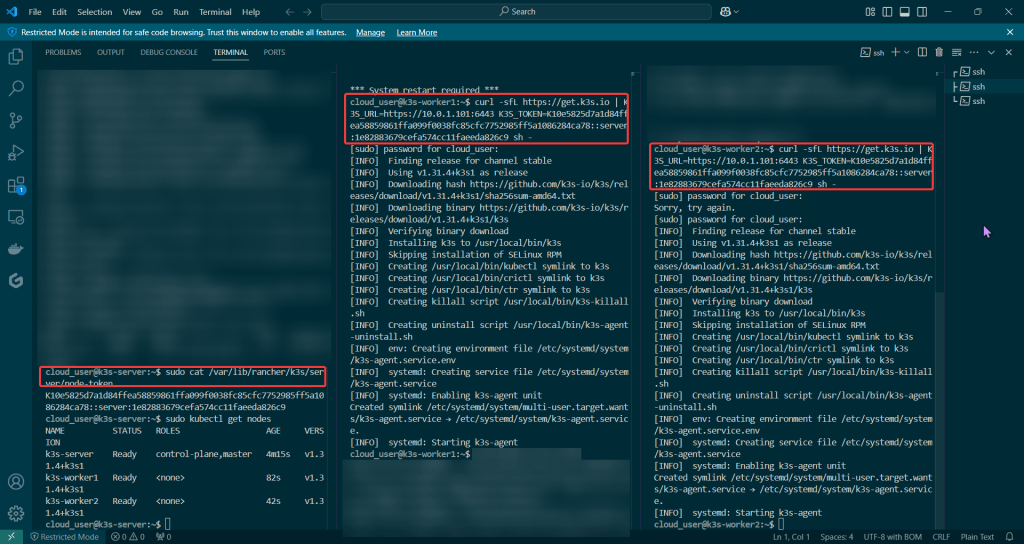
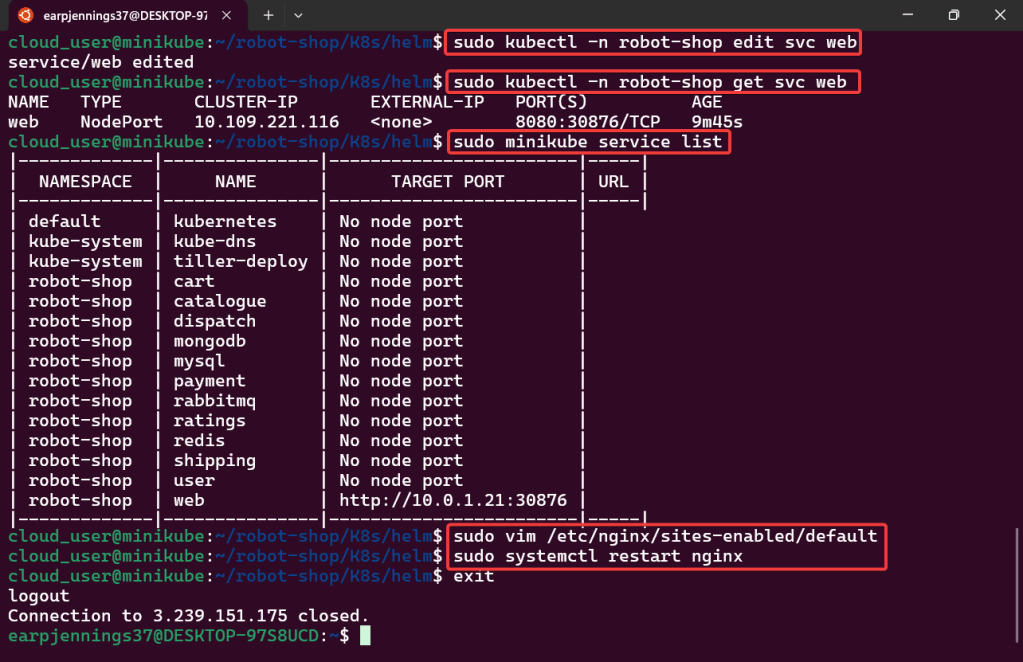
- Please note – there are two (2) controllers, two (2) workers, & an Kubernetes API Load Balancer
Lessons Learned:
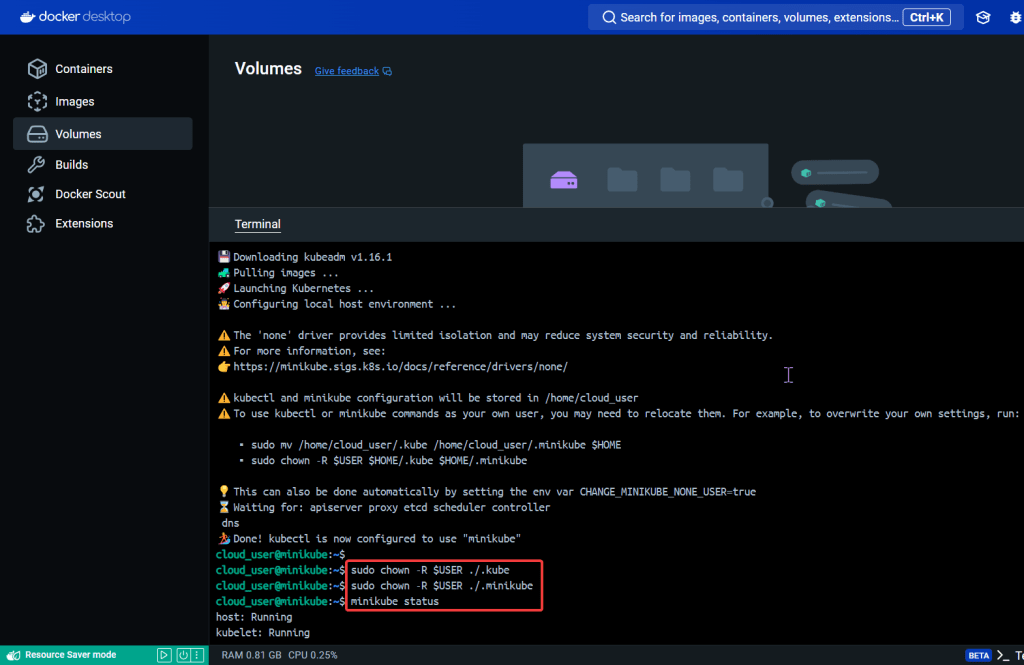
- Permit/Provision CA
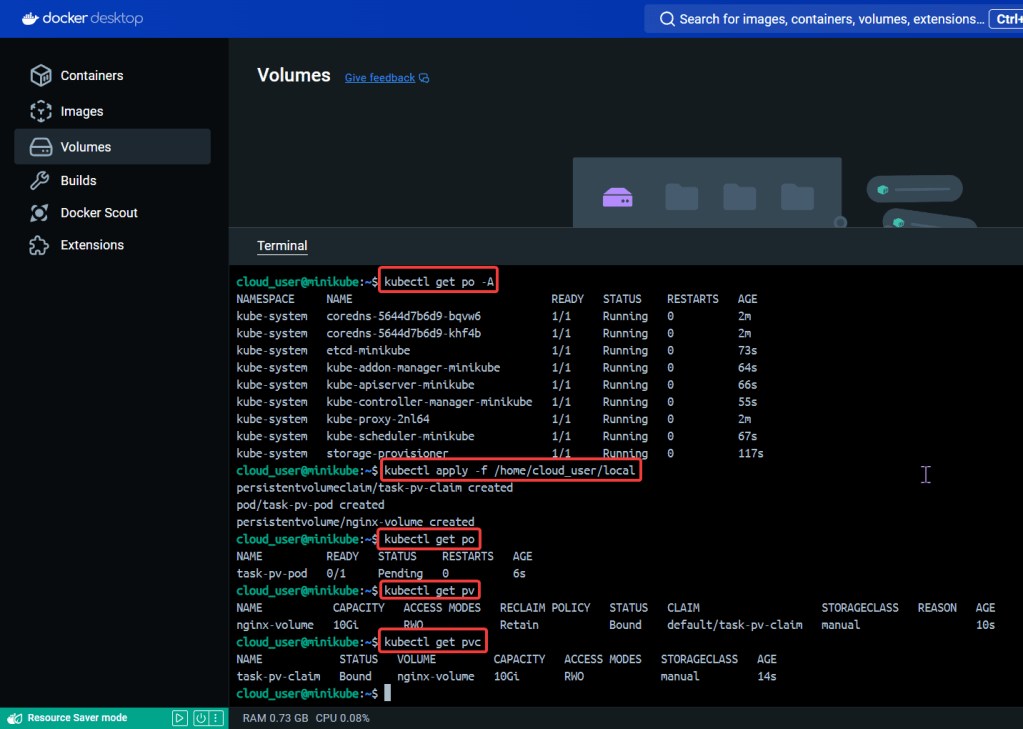
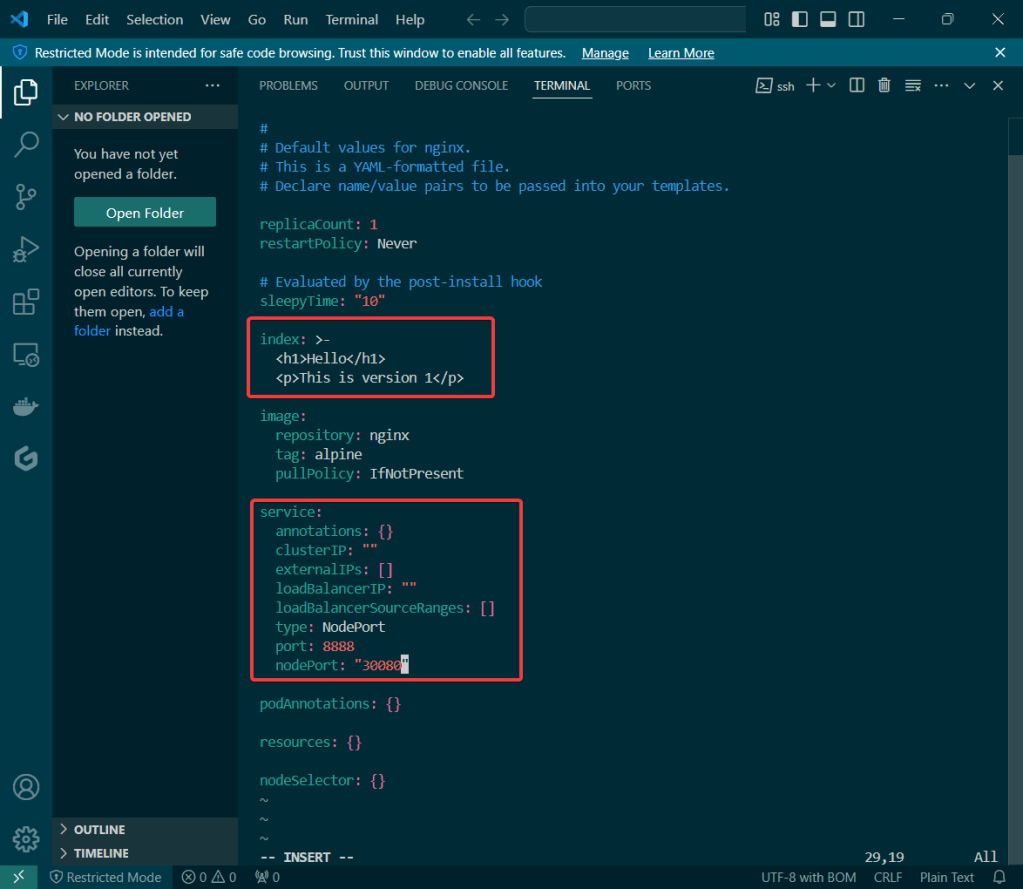
- Create Kubernetes client certs & kubelet client certs for two (2) nodes:
- Admin Client Certificate
- Kubelet Client Certificate
- Manager Client Cert
- Kube-Proxy Client Certificate
- Kube-Scheduler Client Certificate
- Kubernetes API server certificate
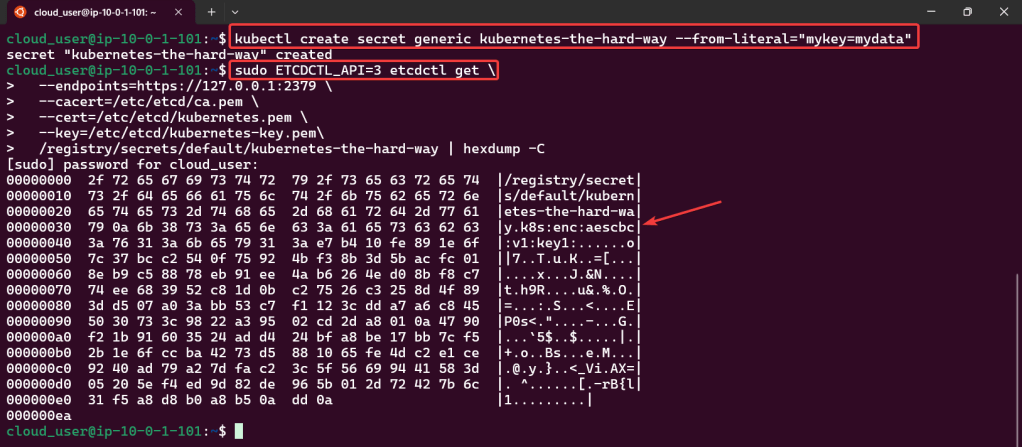
- Kubernetes service account key pair

- If you follow these lessons learned, you will not let this happen to you – don’t be Karen.
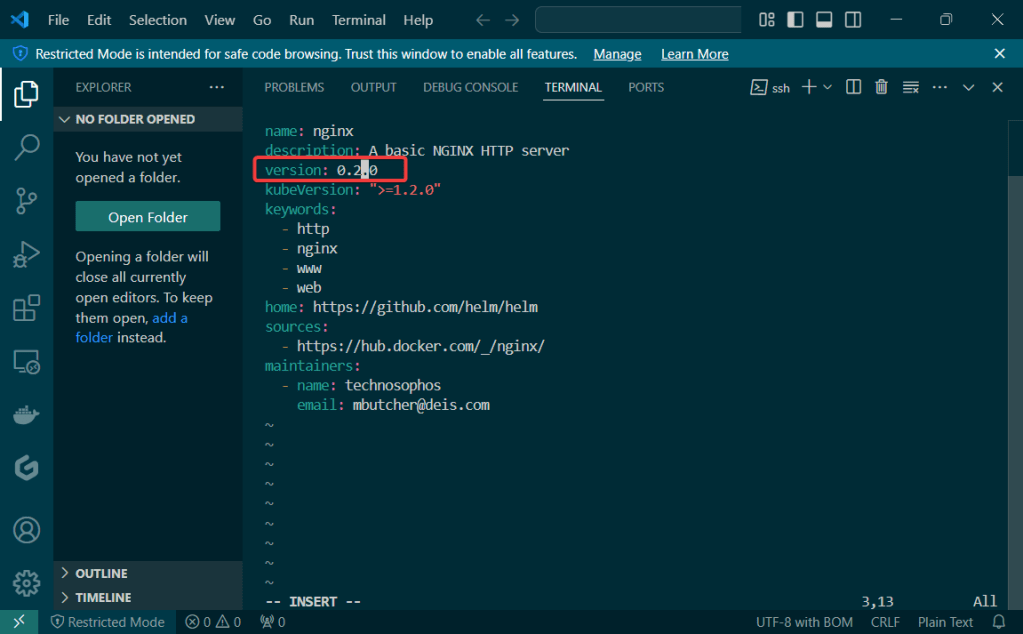
Permit/Provision CA:
- Created to sign other certificates & other certs can now use the CA to show legitness (its a word, look it up in the dictionary..urban, dictionary..) that no fakers are occurring

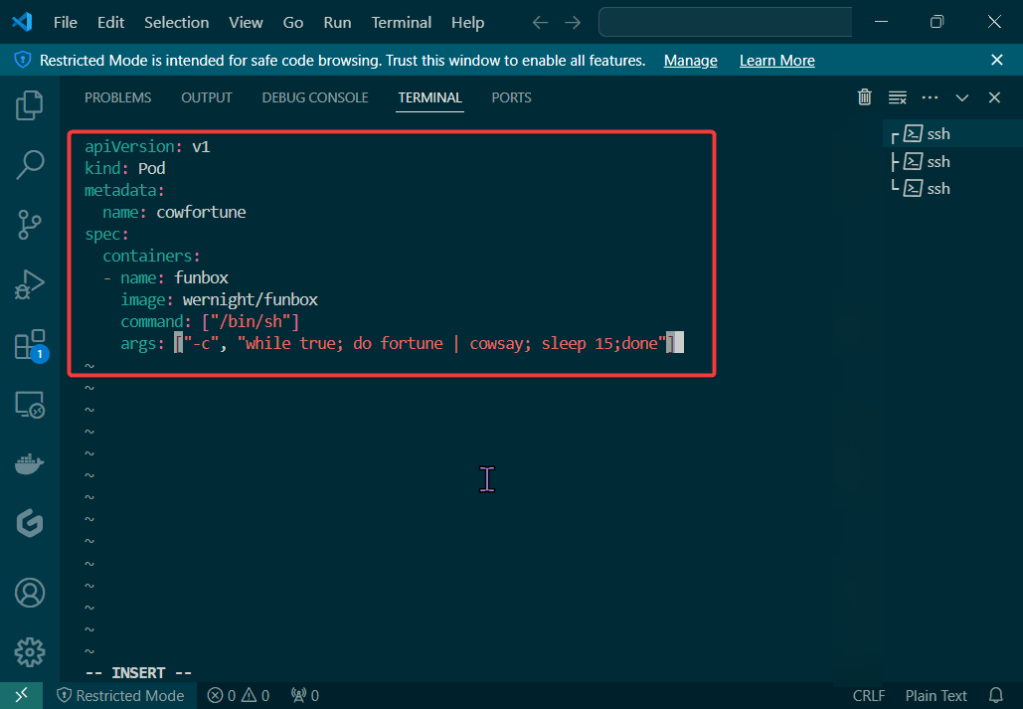
Create Kubernetes client certs & kubelet client certs for two (2) nodes:
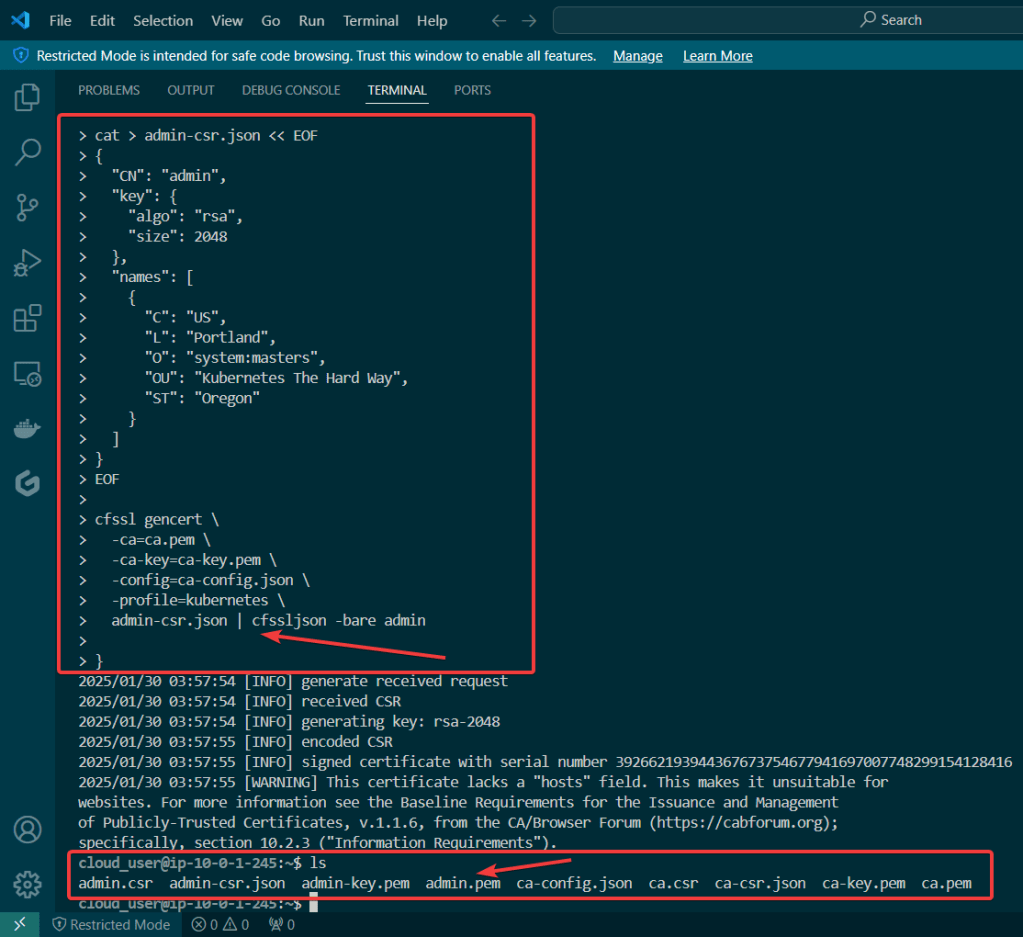
Admin Client Certificate:
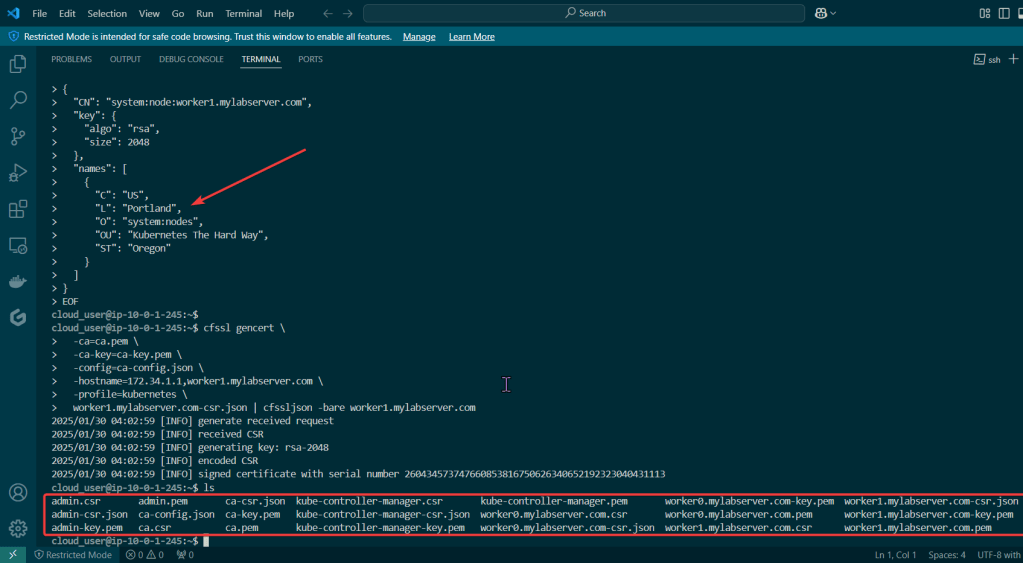
Kubelet Client Certificate:
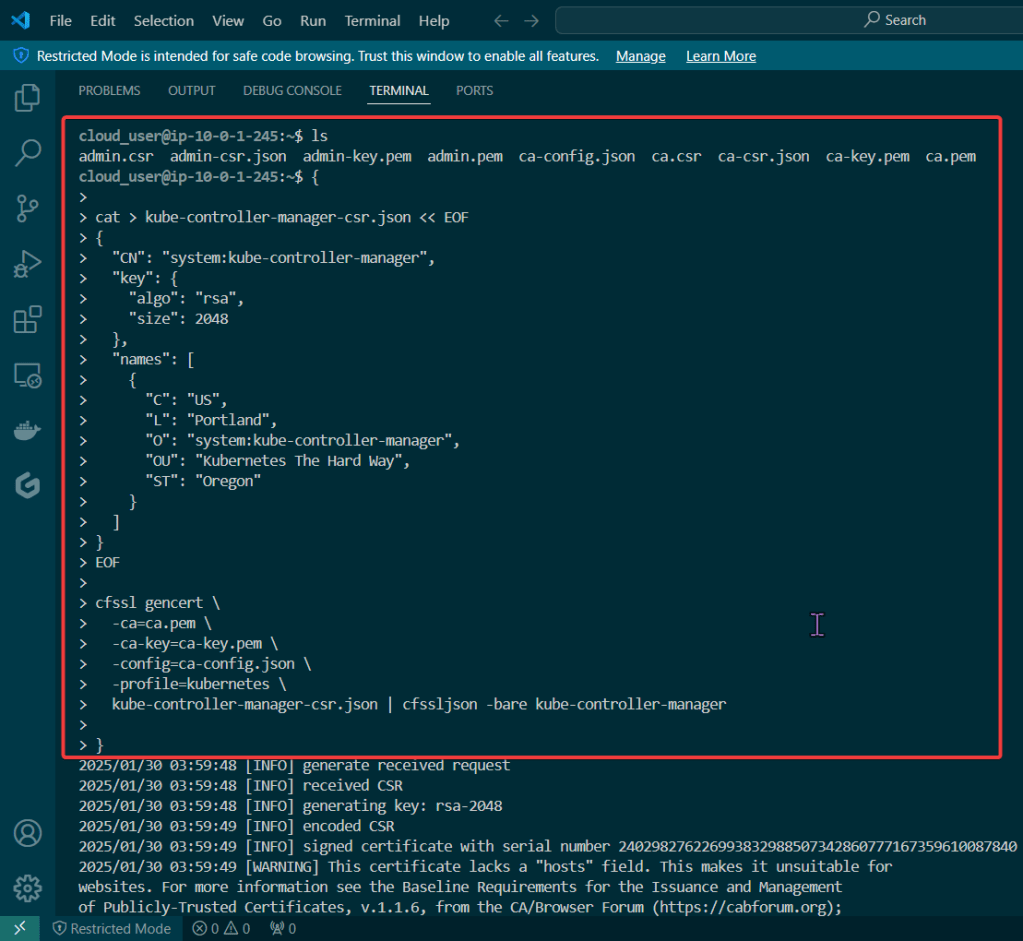
Manager Client Cert:
Kube-Proxy Client Certificate:
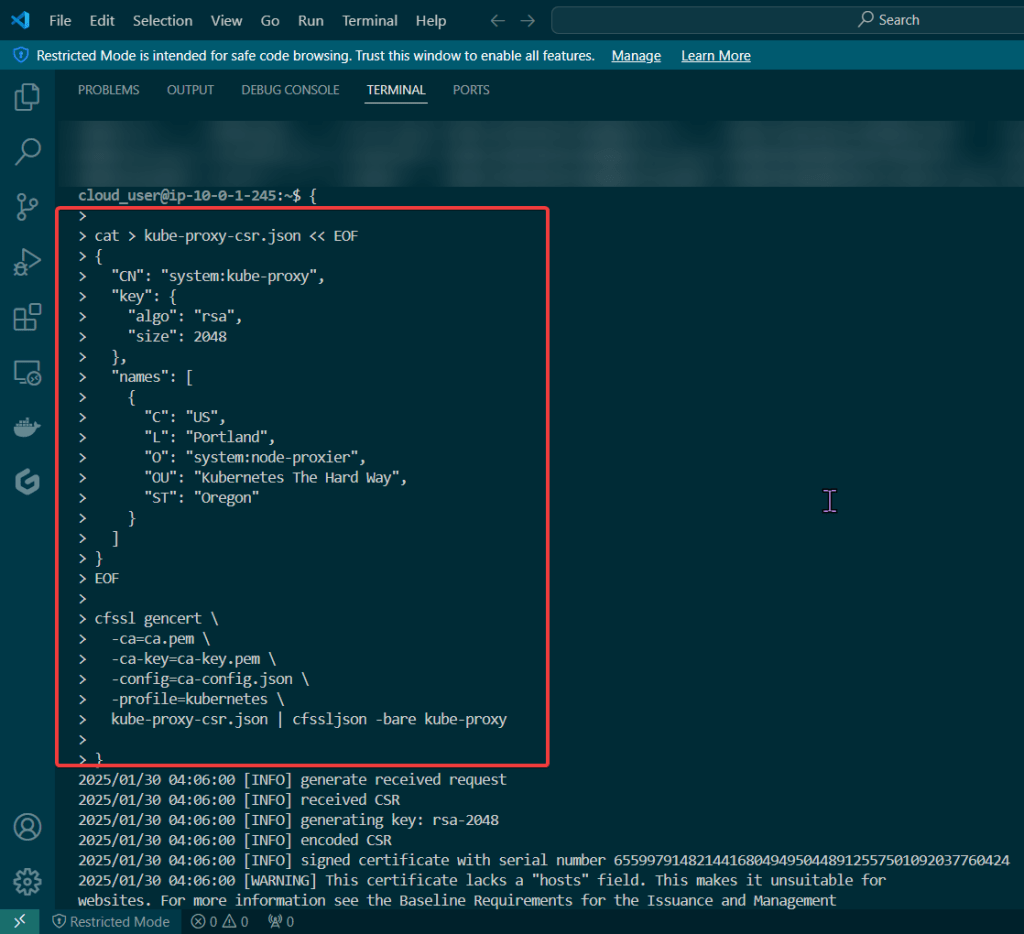
Kube-Scheduler Client Certificate:
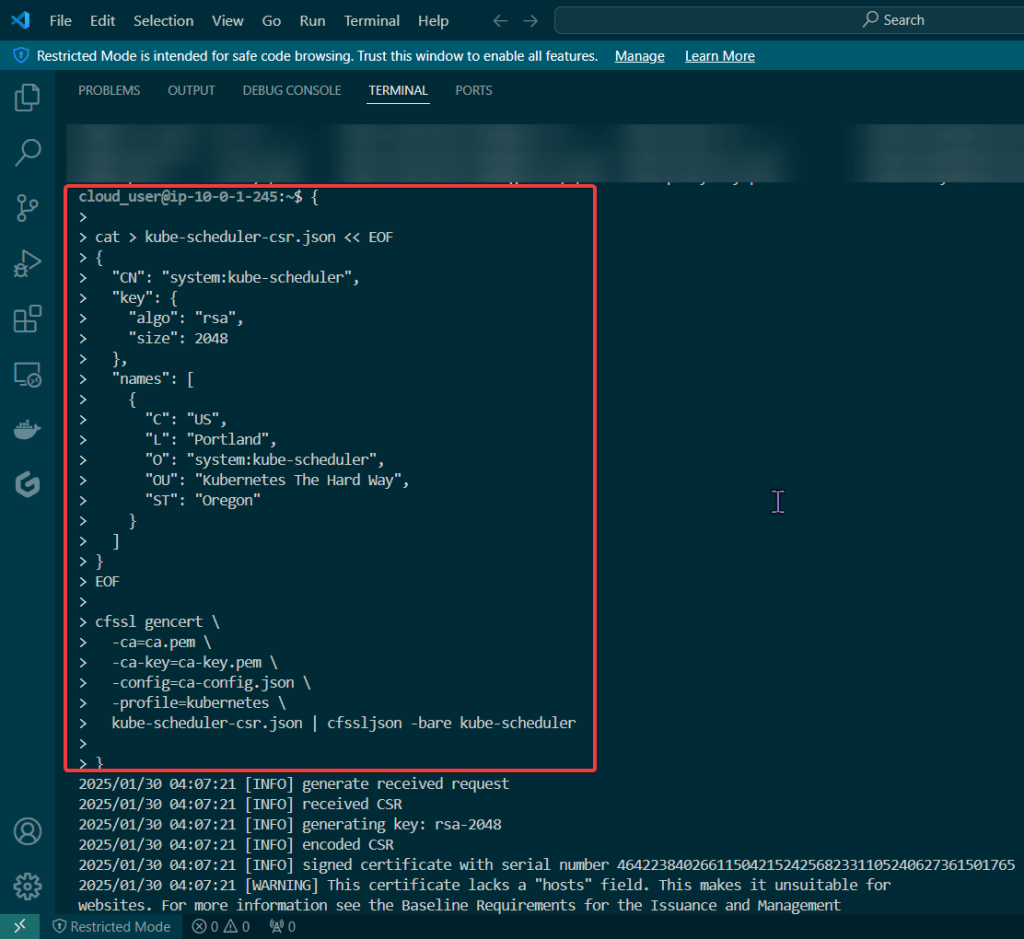

- These gifs are TOOOOO good for info commercial’s in the late 90s’/early 2000s’
Create Kubernetes API server certificate:
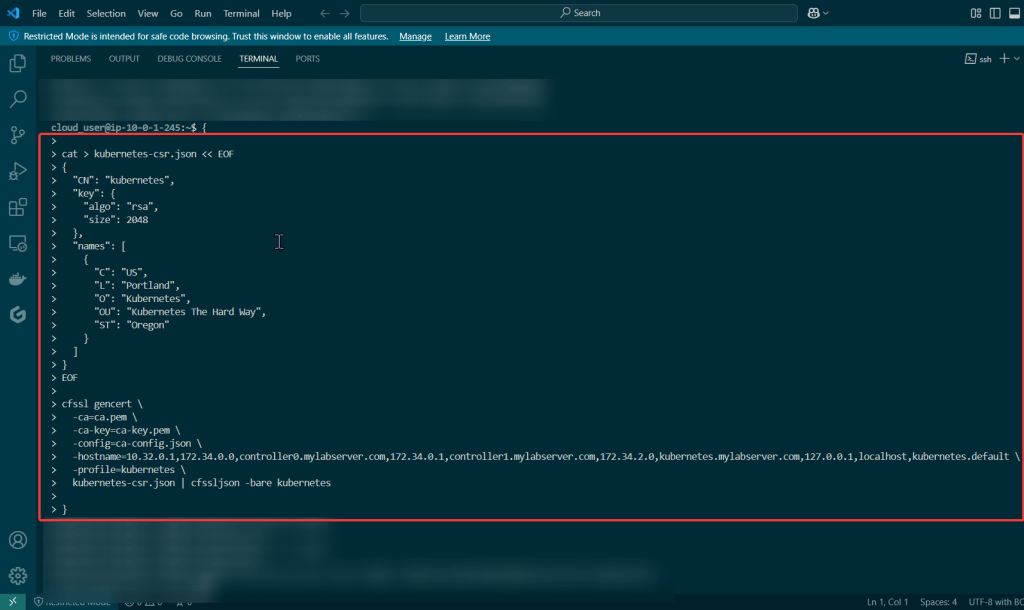
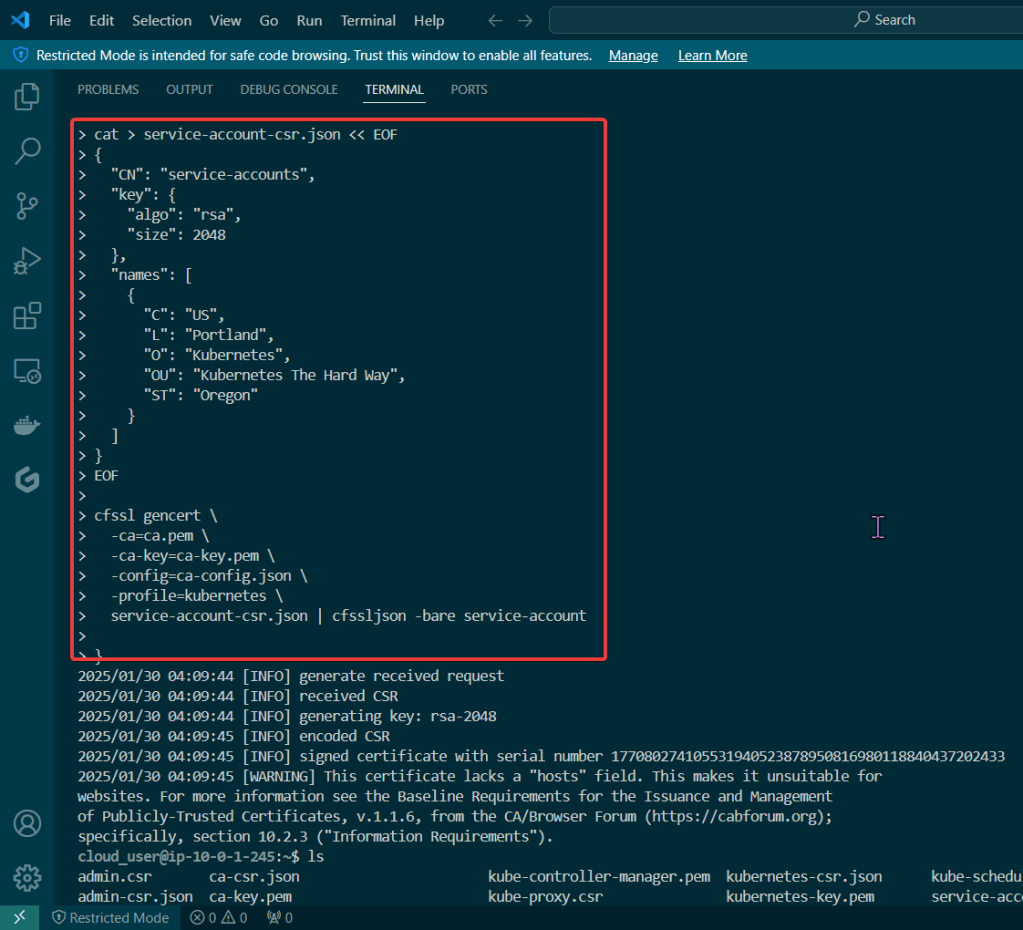
Create Kubernetes service account key pair: