Goal:
Uhh-ohh, we let the newbie drive & were off the road… lets take a peak under the hood & see why we can’t connect to the internet. We understand why an instance cant connect to internet. This post should share an order of operations if one does not know why an instance is not connecting to the internet.
Lessons Learned:
- Determine why instance cant connect to internet
- ID issues preventing instances from connecting to the internet
- Important Notes:
- We have 3 VPCs w/SSH connection & NACLs configured through route table
- Instance 1 & 2 have connection to internet & are a-okay…
- Instance 3 is not connected to the internet, so we outtah’ figure out the problem.
Order of Operations:
- Instance
- Security Group
- Subnet
- NACL
- Route table
- Internet gateway
Solution:
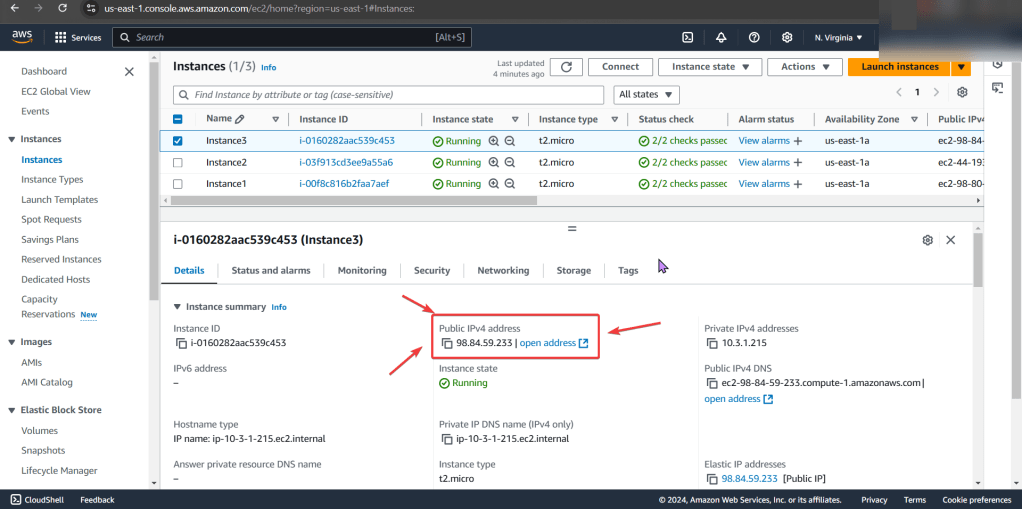
- Instance
- No public IP address
- NACL
- Deny rules for inbound & outbound that prevents all pinging & traffic to instance
- Route Table
- Did not have route to internet gateway
Determine why instance cant connect to internet:
Instance:
- Start w/networking & manage IP address
- See no public IP address below in screenshot
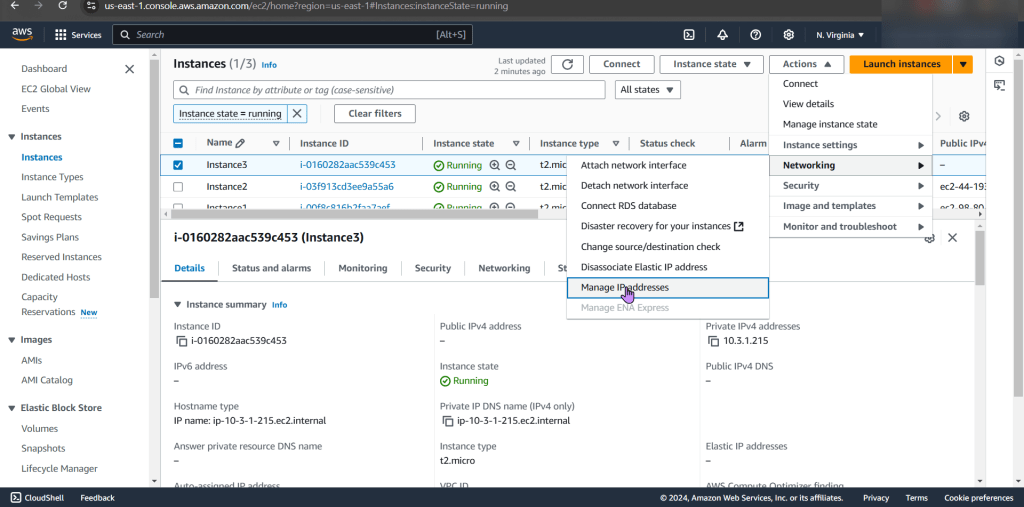
- Wham bam thank ya mam! Fixed!… Wait, it isn’t?
Security Group:
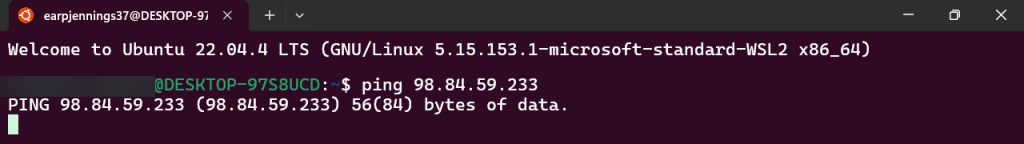
- Can we ping the instance?
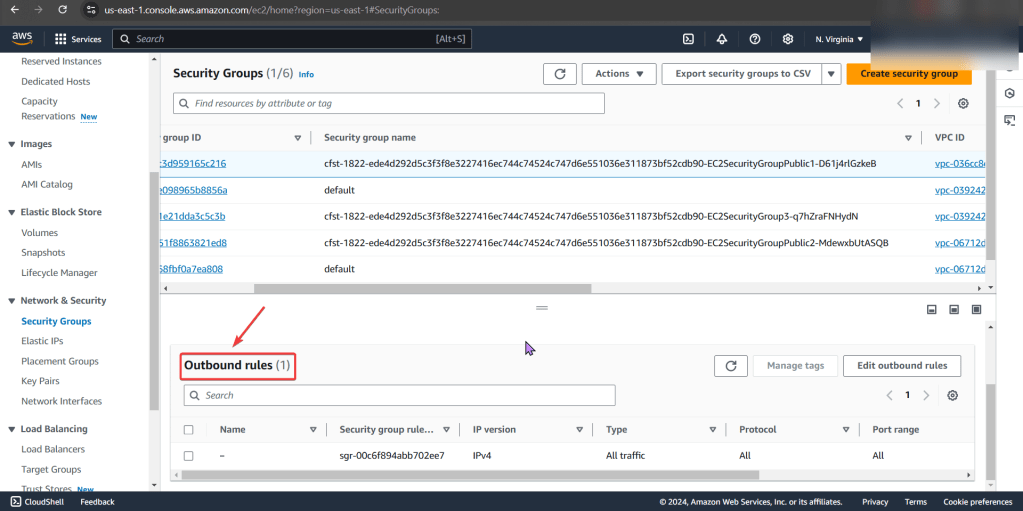
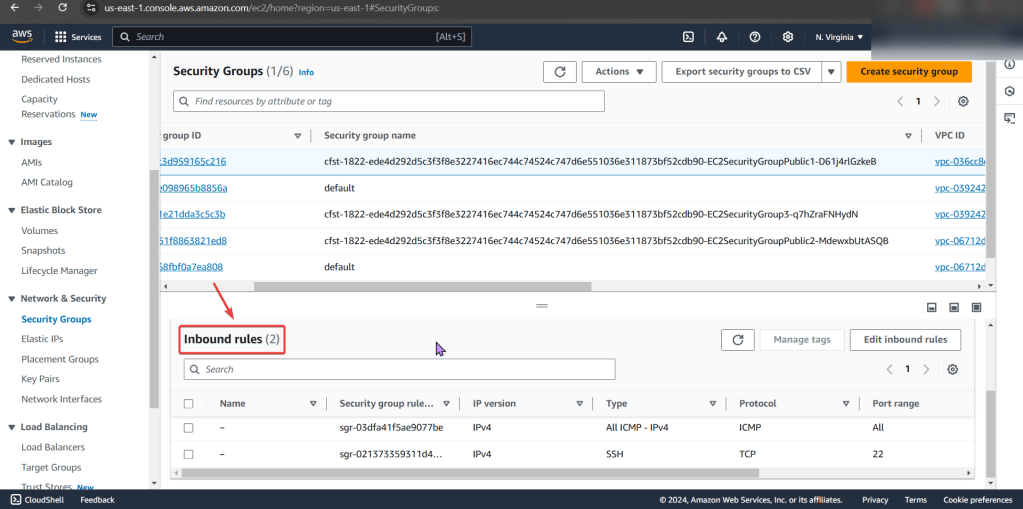
- Remember when looking at rules, just cuz says private – doesn’t mean it is! So check the inbound/outbound rules details
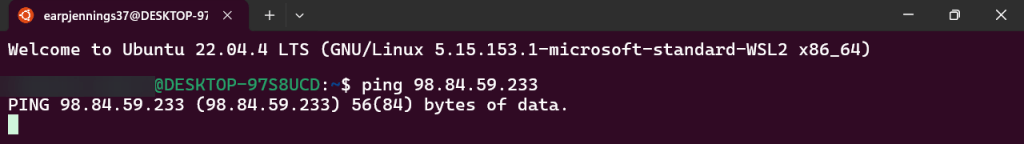
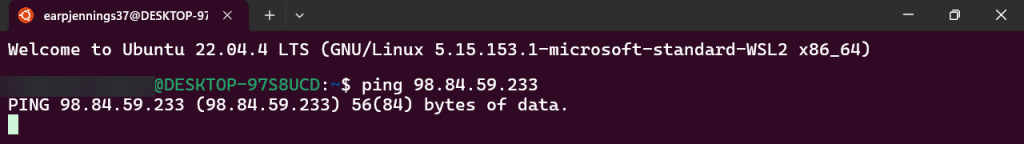
PING!
- Nothing. Okay, I reckon to keep lookin..
Subnet:
- Look at private IP address & then VPC
- Specifically under subnets pay attention to the VPC ID
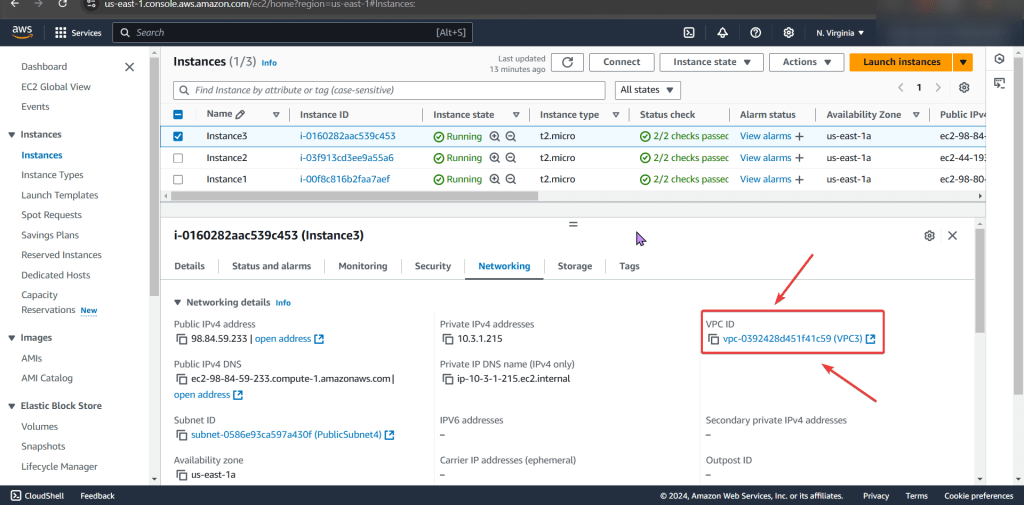
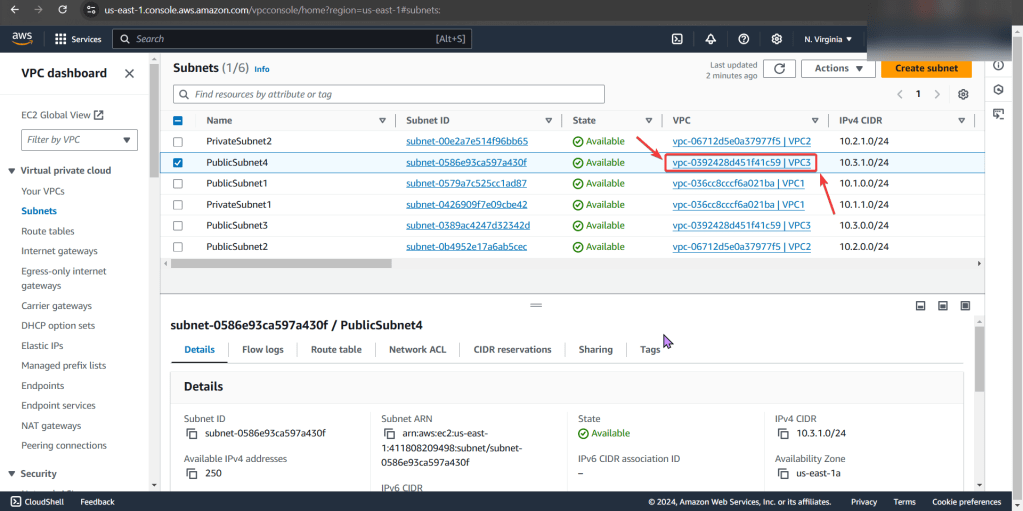
- Looks okay so far, keep on keepin on!
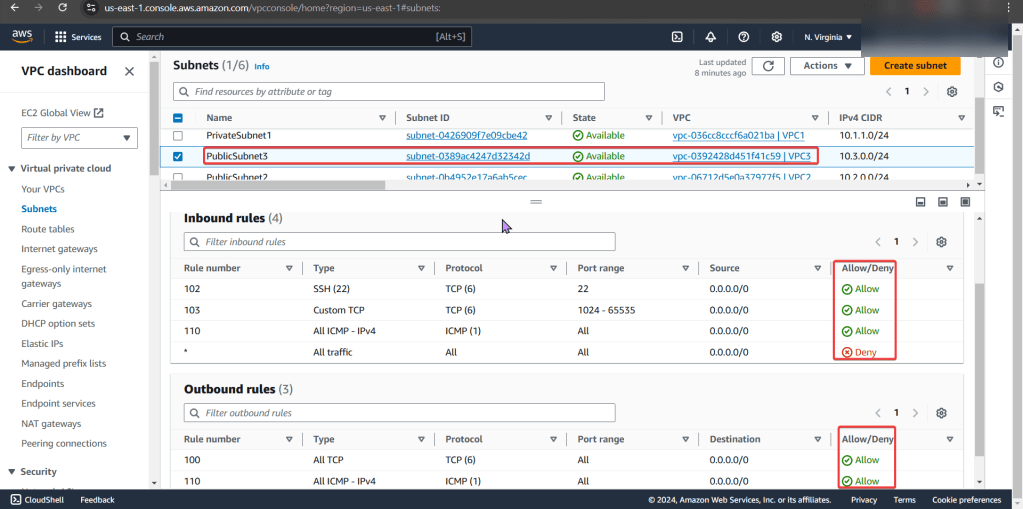
NACLs:
- We found the issue!! The NACL rules deny all inbound/outbound traffic into the instance!
- Even tho the security group does allow traffic, remember the order of operations from in-to-out..
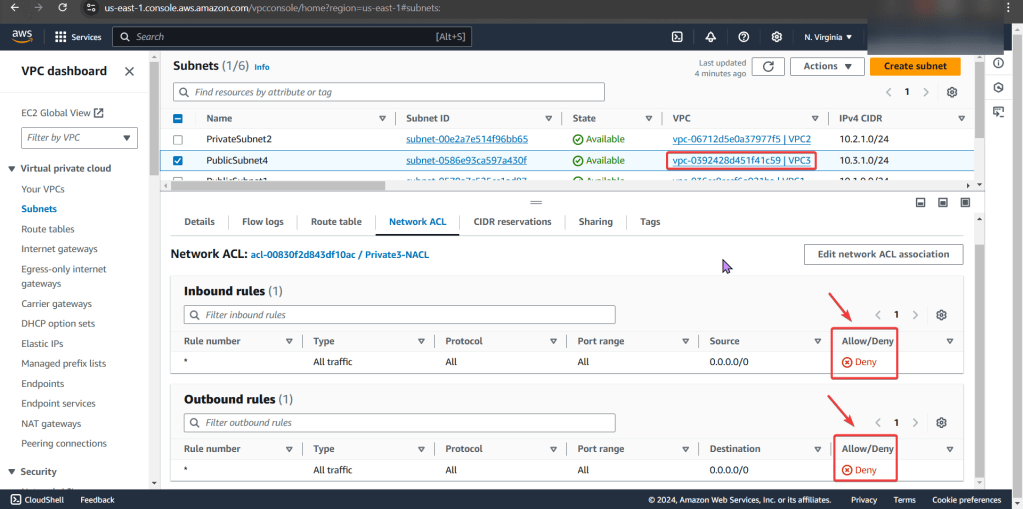
PING!!
- Still nothing, hmm..
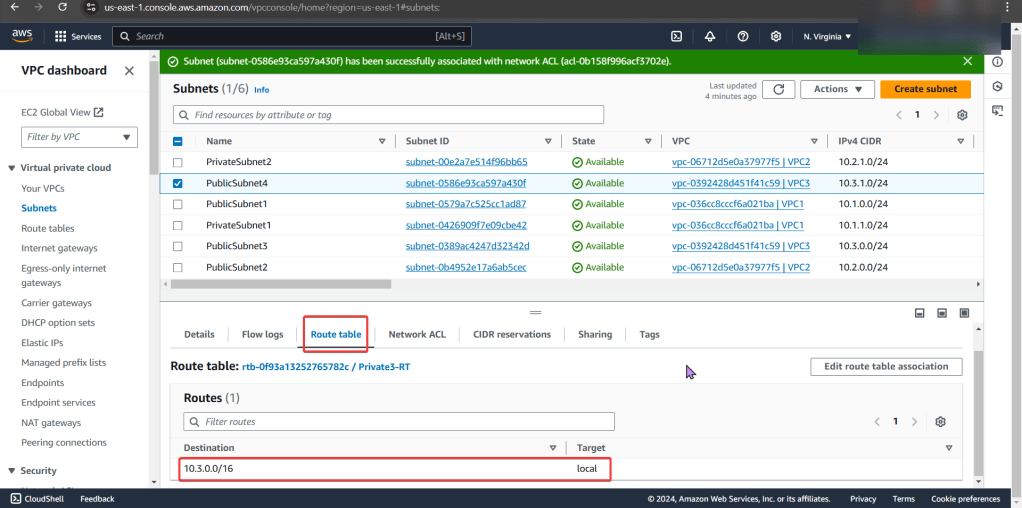
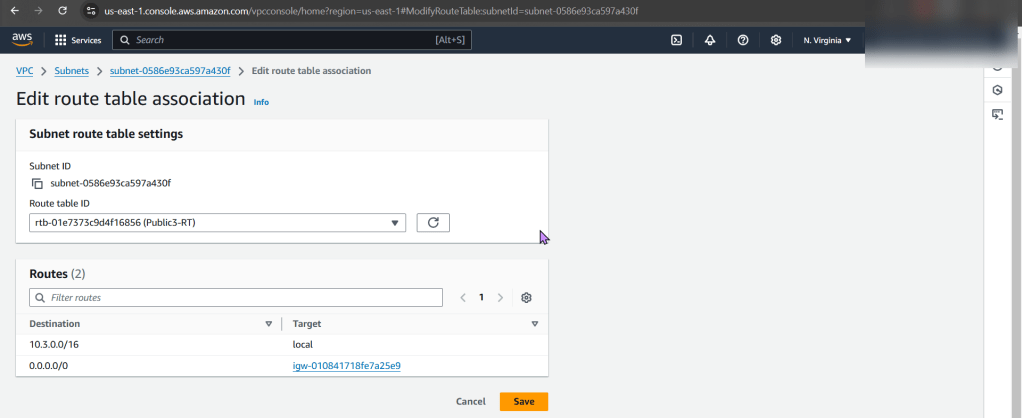
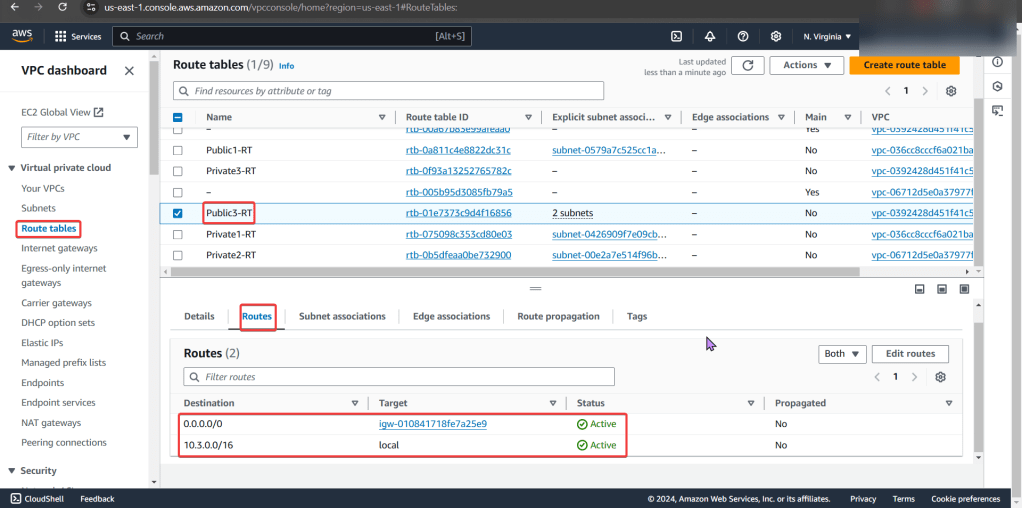
Route Table:
- Ah-ha! We found the issue…again!
- There is no route to the internet gateway
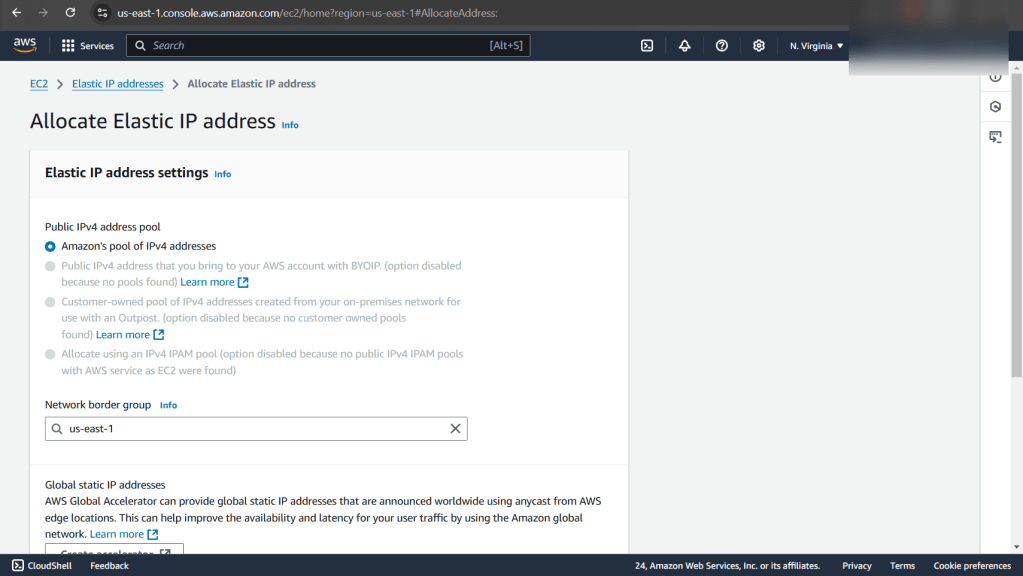
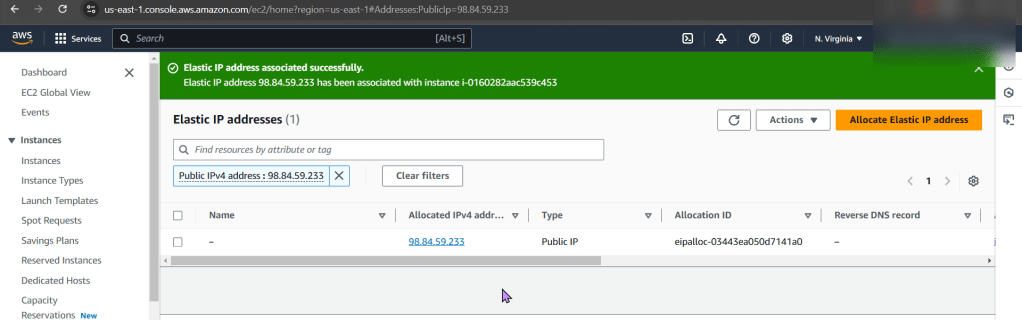
ID issues preventing instances from connecting to the internet:
Instance:
- Allocate an Elastic IP Address, not a public one!!
NACLs:
- The options we have are:
- Change the NACL security rules
- Get a different NACL w/proper rules in it
- In prod… dont do this cuz it can affect all the subnets inside of it.
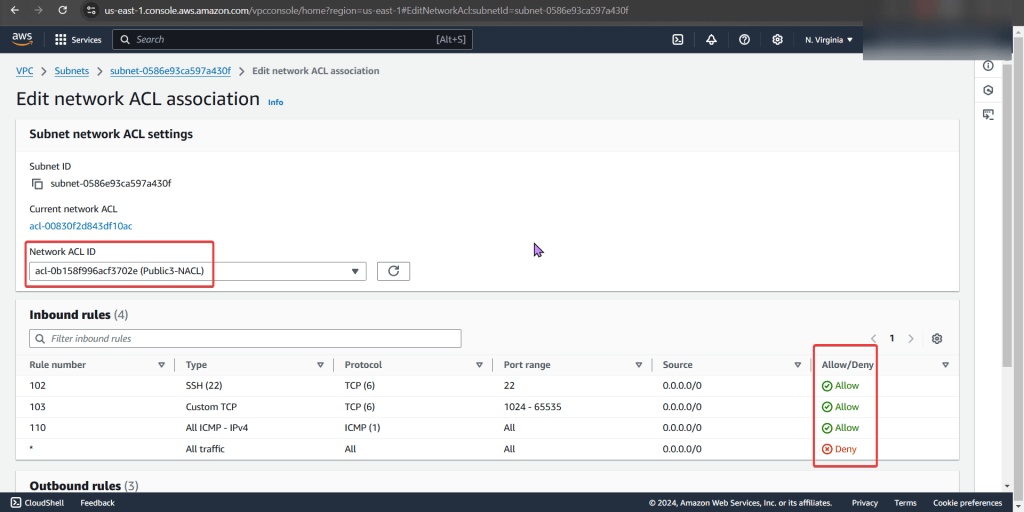
- Under public-subnet4 (which was the original VPC ID we had for instance 3), select edit network ACL association, & change to the NACL to the public-subnet3
Route Tables:
- The options we have are:
- Add a route to the table that allows traffic to flow from subnet to internet gateway
- Remember in other environments, there maybe others using this route table only permitting private access, so not modify.
- Select route table that has appropriate entries
- Add a route to the table that allows traffic to flow from subnet to internet gateway
- Here we edit the route table association & then notice the difference in the route table permitting connection/traffic
Ping!
- YEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEET!!


- Now if you desired you can SSH into the instance
